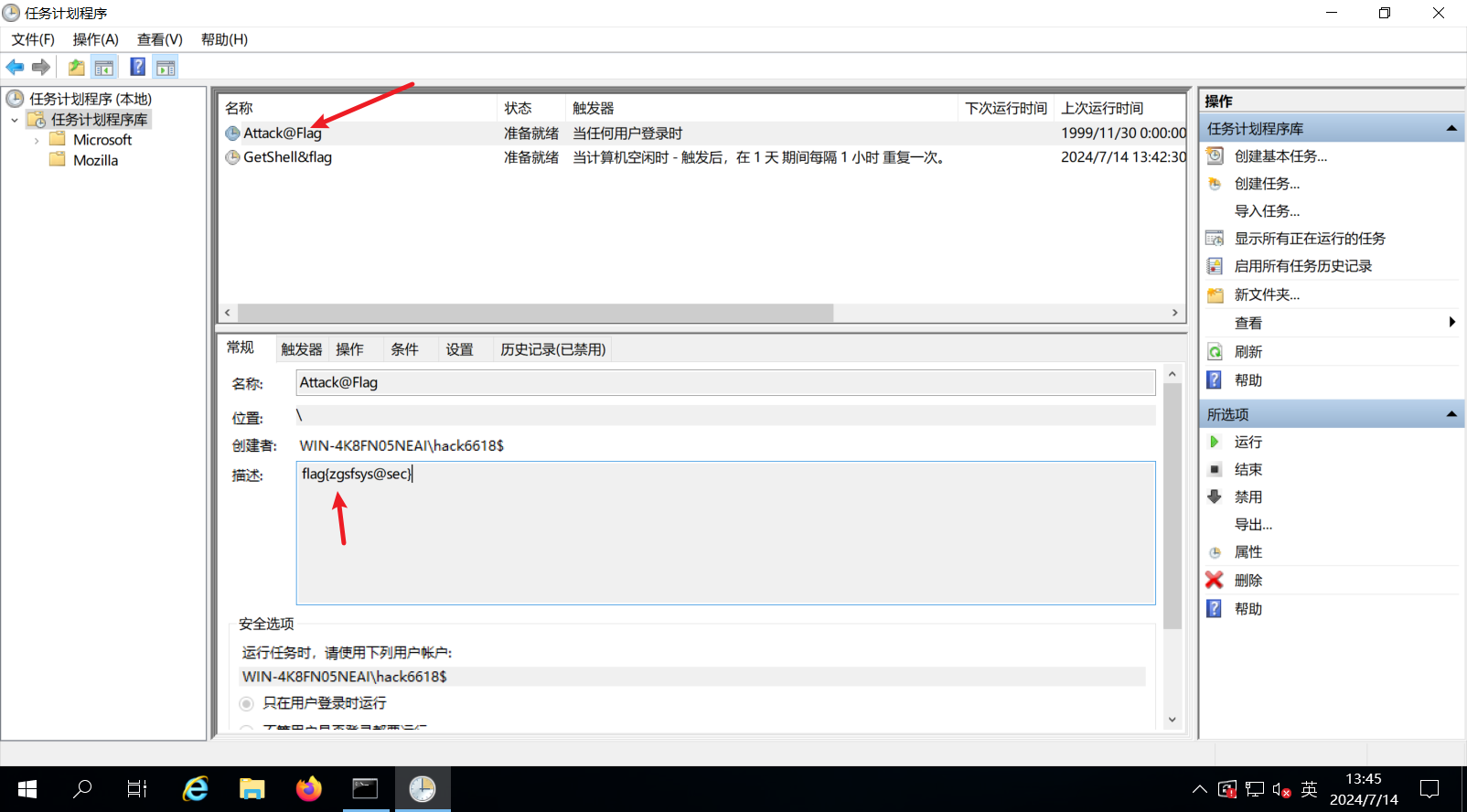
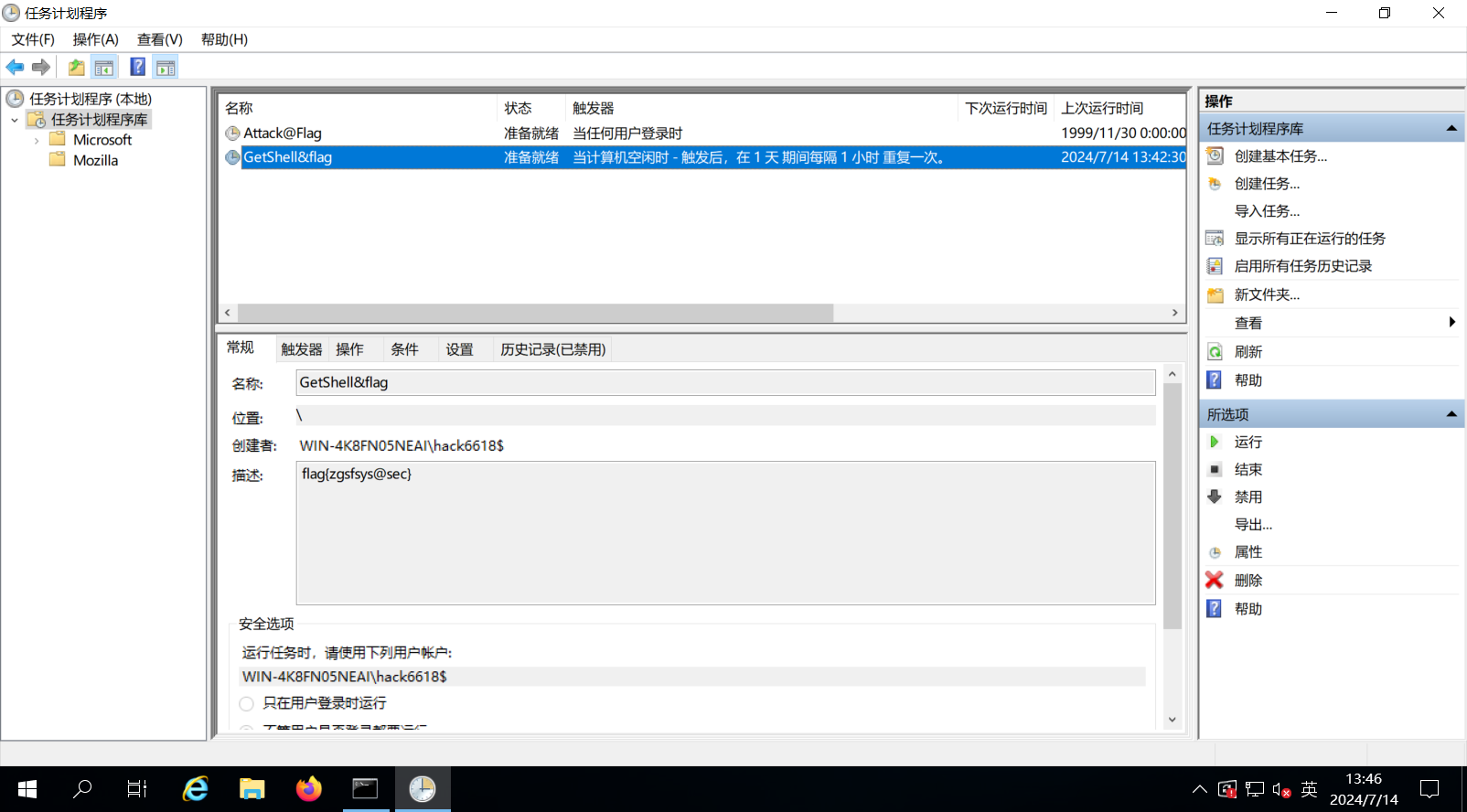
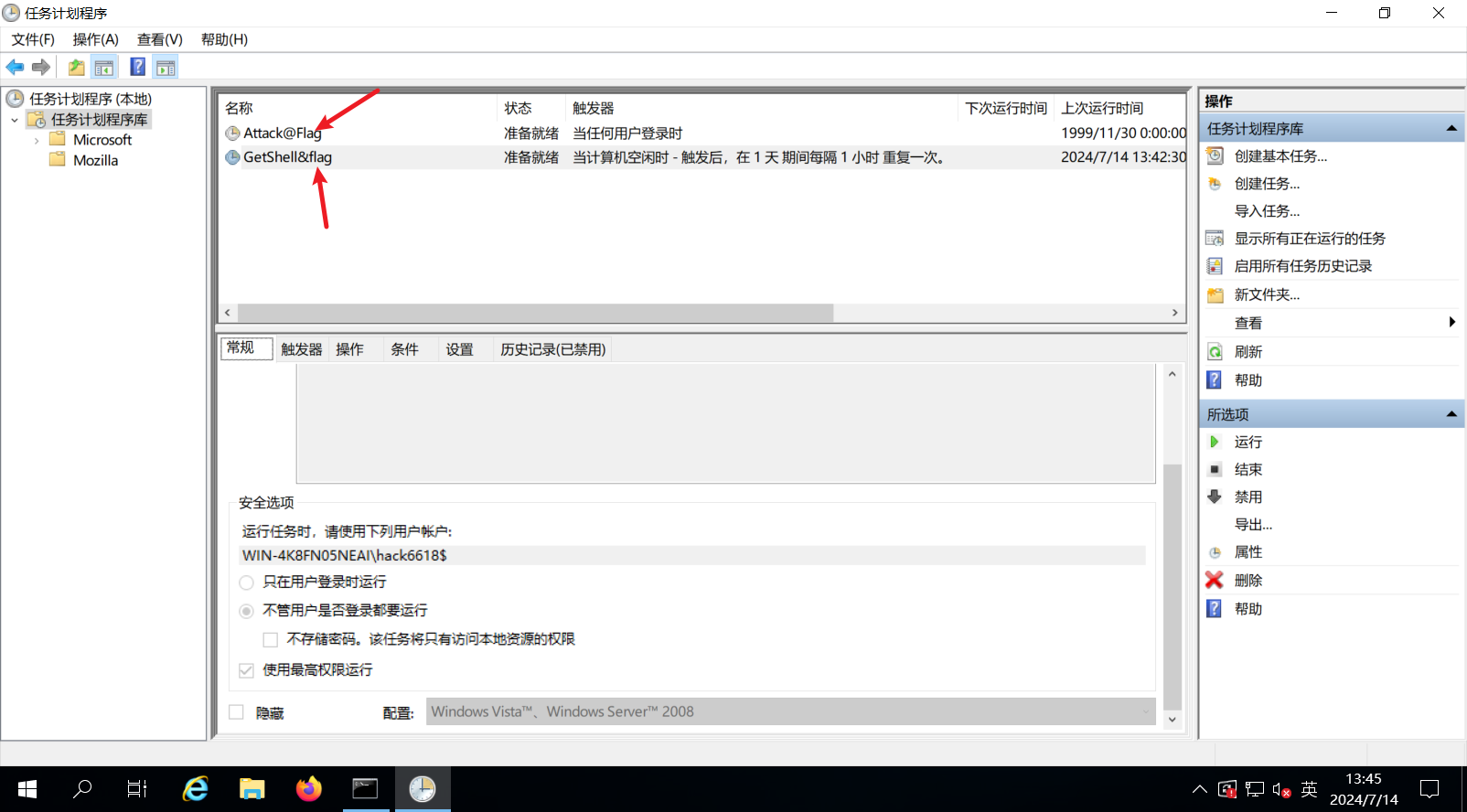
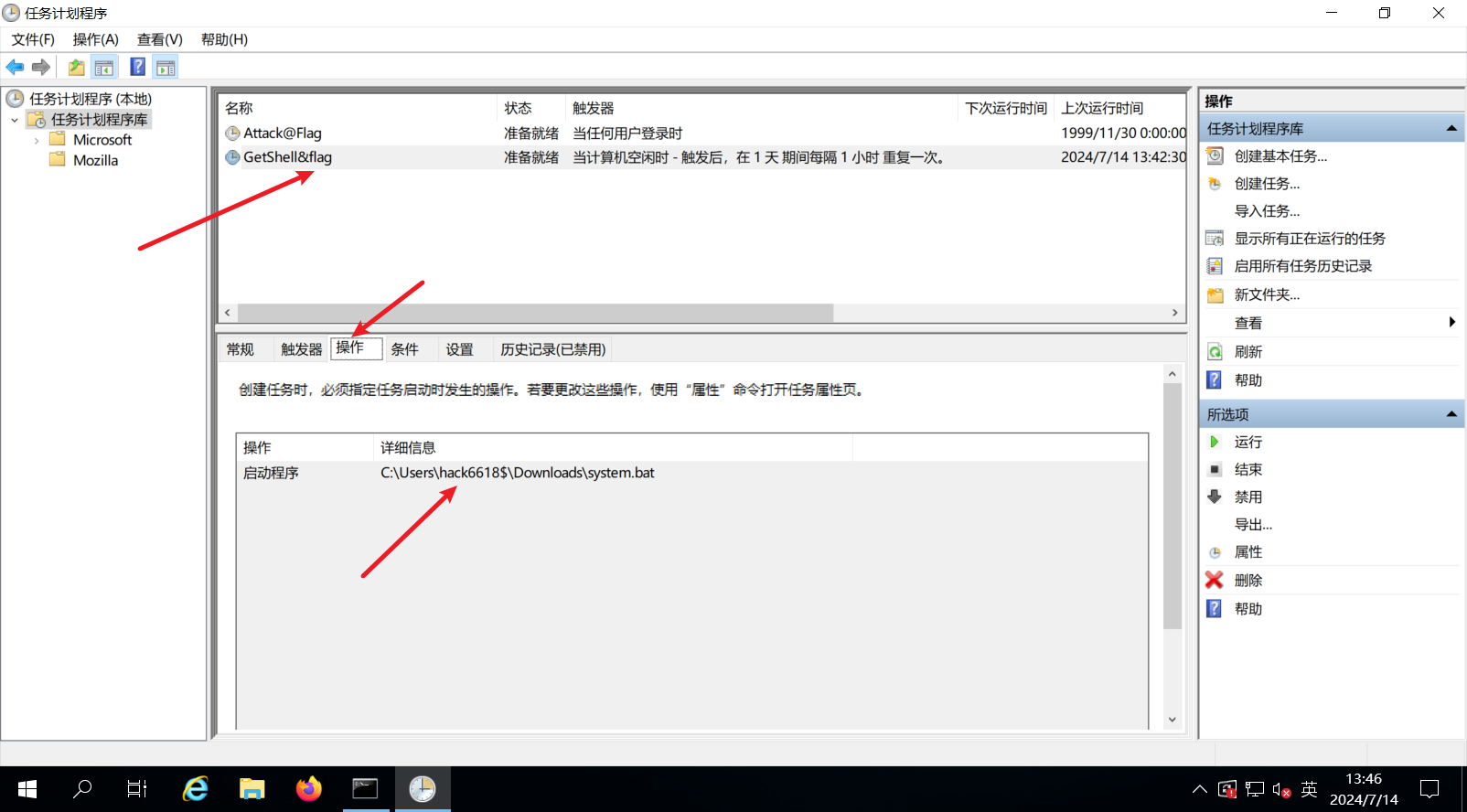
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
| tasklist
映像名称 PID 会话名 会话
========================= ======== ================ =========== ============
System Idle Process 0 Services 0 8 K
System 4 Services 0 140 K
Registry 88 Services 0 23,112 K
smss.exe 292 Services 0 1,384 K
csrss.exe 376 Services 0 5,448 K
wininit.exe 480 Services 0 6,908 K
csrss.exe 488 Console 1 5,636 K
winlogon.exe 548 Console 1 17,548 K
services.exe 616 Services 0 8,612 K
lsass.exe 636 Services 0 16,996 K
svchost.exe 744 Services 0 23,604 K
fontdrvhost.exe 772 Console 1 12,144 K
fontdrvhost.exe 780 Services 0 4,292 K
svchost.exe 864 Services 0 12,892 K
dwm.exe 940 Console 1 73,928 K
svchost.exe 1008 Services 0 87,024 K
svchost.exe 1016 Services 0 13,204 K
svchost.exe 284 Services 0 22,912 K
svchost.exe 676 Services 0 15,060 K
svchost.exe 652 Services 0 45,116 K
svchost.exe 1144 Services 0 33,088 K
WUDFHost.exe 1372 Services 0 8,464 K
svchost.exe 1456 Services 0 24,036 K
svchost.exe 1464 Services 0 9,436 K
svchost.exe 1508 Services 0 6,780 K
svchost.exe 1640 Services 0 16,080 K
svchost.exe 1912 Services 0 7,436 K
spoolsv.exe 2172 Services 0 16,680 K
svchost.exe 2236 Services 0 34,284 K
phpStudyServer.exe 2256 Services 0 9,608 K
VGAuthService.exe 2276 Services 0 11,640 K
vmtoolsd.exe 2312 Services 0 23,212 K
vm3dservice.exe 2324 Services 0 7,220 K
svchost.exe 2364 Services 0 7,892 K
svchost.exe 2372 Services 0 8,640 K
vm3dservice.exe 2488 Console 1 7,884 K
dllhost.exe 2912 Services 0 13,752 K
msdtc.exe 336 Services 0 10,468 K
WmiPrvSE.exe 3232 Services 0 20,868 K
ChsIME.exe 3752 Console 1 14,928 K
svchost.exe 3792 Services 0 14,324 K
sihost.exe 2340 Console 1 24,512 K
svchost.exe 2348 Console 1 31,800 K
taskhostw.exe 3884 Console 1 12,944 K
ctfmon.exe 3696 Console 1 16,616 K
explorer.exe 3880 Console 1 126,116 K
ChsIME.exe 244 Console 1 24,576 K
MusNotifyIcon.exe 2788 Console 1 9,804 K
ShellExperienceHost.exe 4144 Console 1 59,556 K
SearchUI.exe 4264 Console 1 52,164 K
RuntimeBroker.exe 4348 Console 1 20,036 K
RuntimeBroker.exe 4468 Console 1 34,984 K
svchost.exe 4816 Services 0 10,268 K
smartscreen.exe 5068 Console 1 24,328 K
phpstudy_pro.exe 1368 Console 1 62,208 K
RuntimeBroker.exe 3808 Console 1 13,172 K
vmtoolsd.exe 3080 Console 1 40,308 K
cmd.exe 3848 Console 1 4,272 K
conhost.exe 4660 Console 1 43,860 K
svchost.exe 2524 Services 0 12,220 K
taskhostw.exe 184 Console 1 11,936 K
svchost.exe 4592 Services 0 10,912 K
TrustedInstaller.exe 4836 Services 0 7,204 K
TiWorker.exe 3280 Services 0 10,228 K
WmiPrvSE.exe 2652 Services 0 8,512 K
taskhostw.exe 4172 Services 0 7,280 K
tasklist.exe 1204 Console 1 7,868 K
|